Scenario
Jake, a Transgear Corp Incident Response analyst, delves into an alert from Brianna, who flagged unusual activity on her workstation. A week prior, enticed by an email promising Amazon gift cards, Brianna clicked a link, unknowingly downloading malware. This granted attackers access, enabling espionage: capturing credentials, file copying, and eavesdropping on video calls. Days later, Brianna noticed her workstation lagging and received a LinkedIn login attempt notification from an unfamiliar device. Worried, she reported to the IT help desk. Jake now investigates to find and collect IOCs.
Tools: Wireshark, TCPdump, CyberChef, Mitre IDs T1566 , T1204
What time did the suspected user system/browser connect to the malicious website? (Format: XX:XX:XX:XXXXXX)
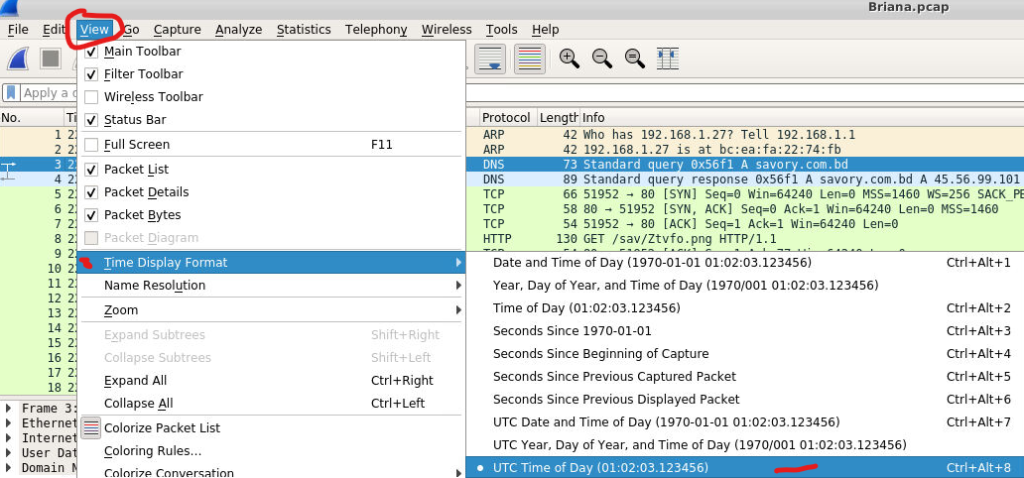
After opening the Briana.pcap file on the desktop, I adjusted Wireshark’s time format from Seconds Since Beginning of Capture to UTC Time of Day.
I then proceeded to analyze the packets and identified a DNS log in the third packet.

This revealed a DNS query to savory[.]com[.]bd, so I used the UTC timestamp from that specific packet as the answer: 22:51:00.220437.
Q2 What is Briana’s IP address? (Format: IP Address)
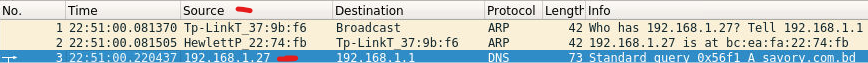
I reanalyzed the DNS packet and located the Source IP, which was listed as 192.168.1.27.
Q3) What is Briana’s MAC/Ethernet address? What is the vendor name for the MAC address? (Format: MAC, Vendor Name)
I examined the packets preceding the DNS protocol and identified the Address Resolution Protocol (ARP) packets. As explained by Zenarmor, “The ARP protocol is used to resolve the MAC address of a networked device whose IP address is known.”
From this, I observed the device communicating with the router “Tp-LinkT.” When the “Info” field displayed the query ‘Who has 192.168.1.27’, it confirmed that 192.168.1.27 is our host. In Packet 2, I found that the MAC address for 192.168.1.27 is bc:ea:fa:22:74:fb.
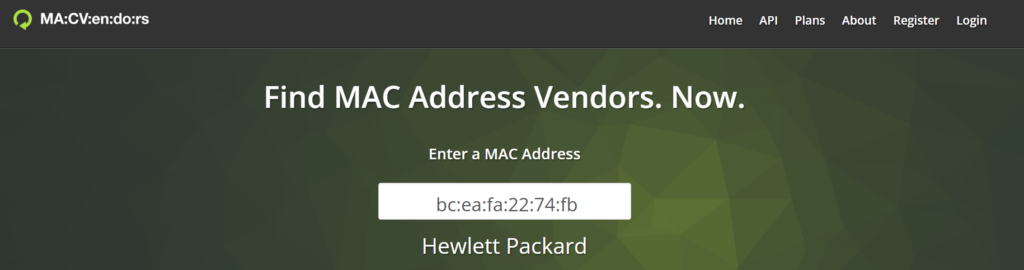
Next, I determined the vendor by inspecting Packet 2, which indicated HewlettP, representing Hewlett-Packard. Therefore, the answer is: bc:ea:fa:22:74:fb, HewlettPackard.
Q4) What is Briana’s Windows machine name? (Format: Machine Name)
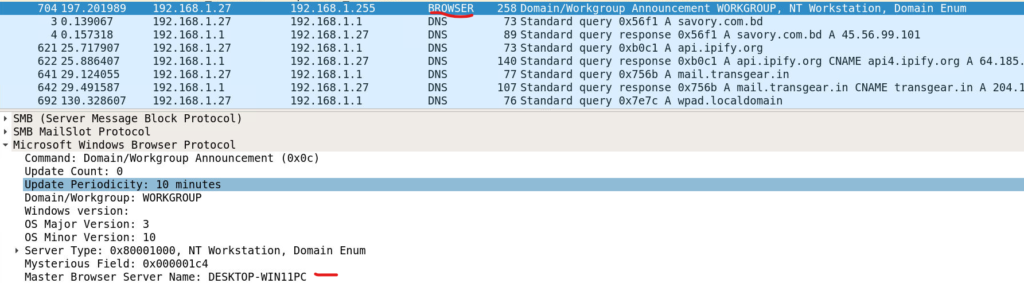
This step took some time, as I didn’t find the information I was looking for in the DNS or NBNS packets. However, I eventually noticed the BROWSER protocol field and decided to investigate further.
In the BROWSER protocol packets, I found the ‘Master Browser Server Name’, which revealed that the host name is DESKTOP-WIN11PC. This serves as another method for identifying the system’s host name.
Q5) What is Briana’s Windows username? (Format: Username)
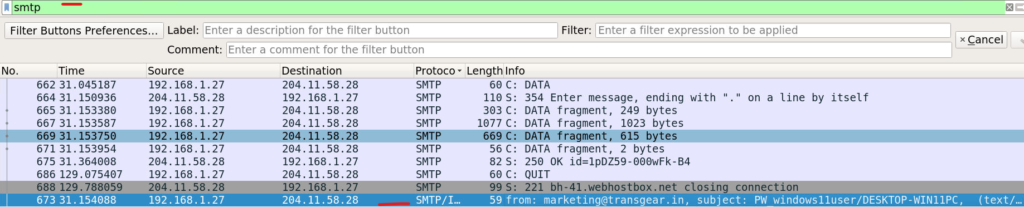
I searched for the SMTP protocol and the final packet in the sequence caught my attention. I expanded the packet and navigated down to the Line-based text data section for further details. There we can see the Username – admin@windows11users.com
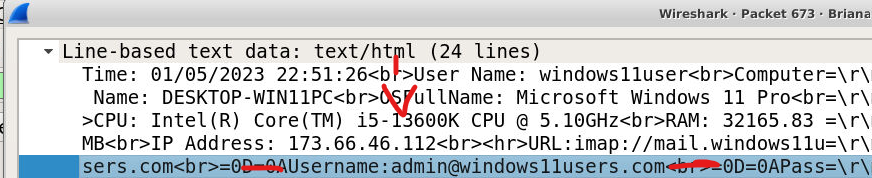
Q6) What email address was the attacker sending data to? (Format: name@domain.tld)

Knowing that the attacker hijacked the email, the SMTP packet also revealed clear text information. Within the Line-based text data, the recipient was identified as zaritkt@arhitektondizajn.com.
Q7) What type of CPU does Briana’s computer use? (Format: CPU Name)

Q8) How much RAM does Briana’s computer have—in GBs? (Format: XXGB)
The RAM size is listed directly after the CPU in MB as 32165.83. To convert it into GB, we divide by 1024 (since 1024MB = 1GB). This gives us:
32165.83 ÷ 1024 = 31.4119433594GB. However, RAM sticks are typically sold in rounded sizes, and it’s unlikely to find a 31.4119433594GB RAM stick. Rounding it up gives a total of 32GB.
Q9) What type of account login data was stolen by the attacker? (Format: Data1, Data2)
Logically, I selected Username and Password as the type of login data stolen. These credentials could easily be decrypted from the clear base64-encoded text using a tool like CyberChef.
What are the username and password related to the Amazon account? (Format: Username, Password)
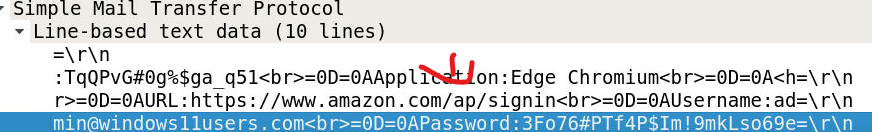
Noticing the Amazon domain in the packet, I followed the trail until I identified the username. The \r\n symbols in the packet represent newlines and carriage returns and are not part of the actual data.
The username, admin@windows11users.com, and the password, 3Fo76#PTf4P$Im!9mkLso69e=, were visible. I attempted to decode the password using Base64, but it appeared to be encrypted. Instead, I used the encrypted version directly on BTLO, and it worked successfully.
Q11) What username did Briana use to authenticate to webhostbox[.]net? Can you decode it? (Format: Username)
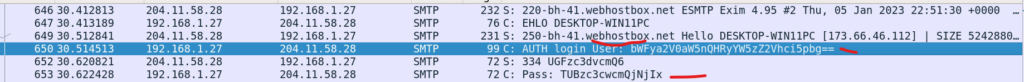
In the SMTP protocol, when connecting to webhostbox, the Auth Login username and Password are Base64-encoded. Decoding the username, bWFya2V0aW5nQHRyYW5zZ2Vhci5pbg==, reveals the email address marketing@transgear.in.
Q12) What password did Briana use to authenticate to webhostbox[.]net? Can you decode it? (Format: Password)
Decoding username and password using cyberchef


