Scenario
The Account Executive contacted the Security Operations Center (SOC), reporting an inability to access files on their computer and a persistent pop-up message stating that their files have been encrypted. This strongly suggests a ransomware attack. The SOC team has disconnected the affected computer from the network and acquired a memory dump of the machine for analysis. Your mission is to investigate the ransomware attack using Volatility, understand how it works, and identify ways to stop it.
Project Workflow
Step 1: Analyze the Memory Dump for Suspicious Activity
- List Running Processes:
- Use Volatility to list all running processes to identify anomalies:bash
-
python3 vol.py -f infected.vmem windows.pslist - Look for:
- Processes with unusual names.
- Recently created processes.
- High privilege levels.
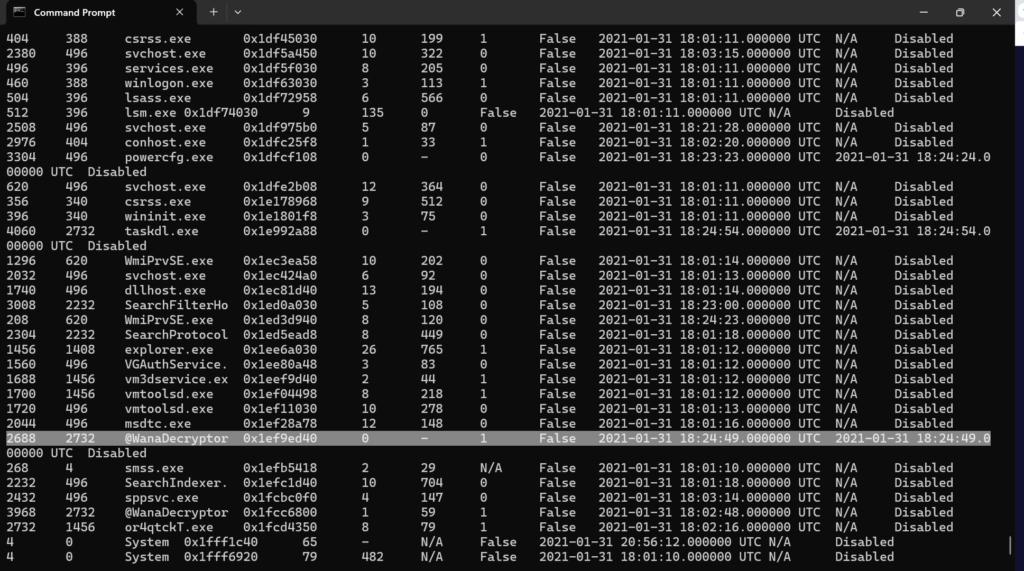
Scrolling to the bottom we can see the suspicious process: @WanaDecryptor
What is the parent process ID for the suspicious process?
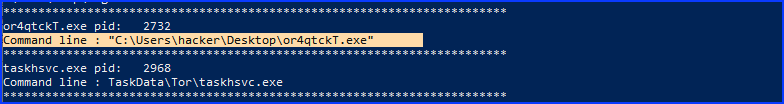
From previous output, we see the parent process ID(PPID) in the 3rd column: 2732
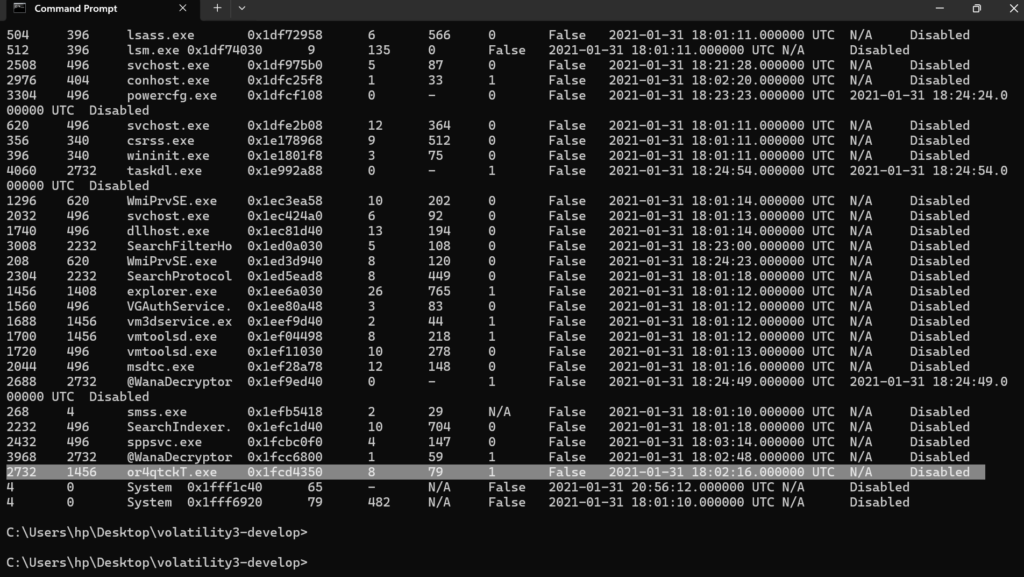
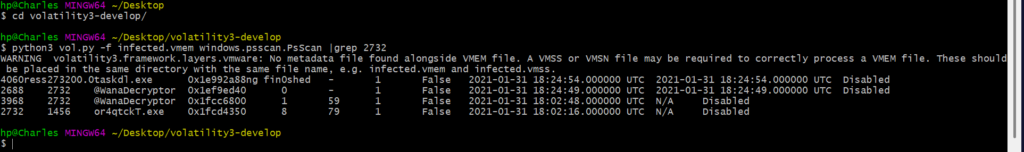
What is the initial malicious executable that created this process?
python3 vol.py -f infected.vmem windows.psscan.PsScan | grep 2732
or4qtckT.exe
If you drill down on the suspicious PID (vol.py -f infected.vmem –profile=Win7SP1x86 psscan | grep (PIDhere)), find the process used to delete files
taskdl.exe
Find the path where the malicious file was first executed
python3 vol.py -f infected.vmem windows.cmdline
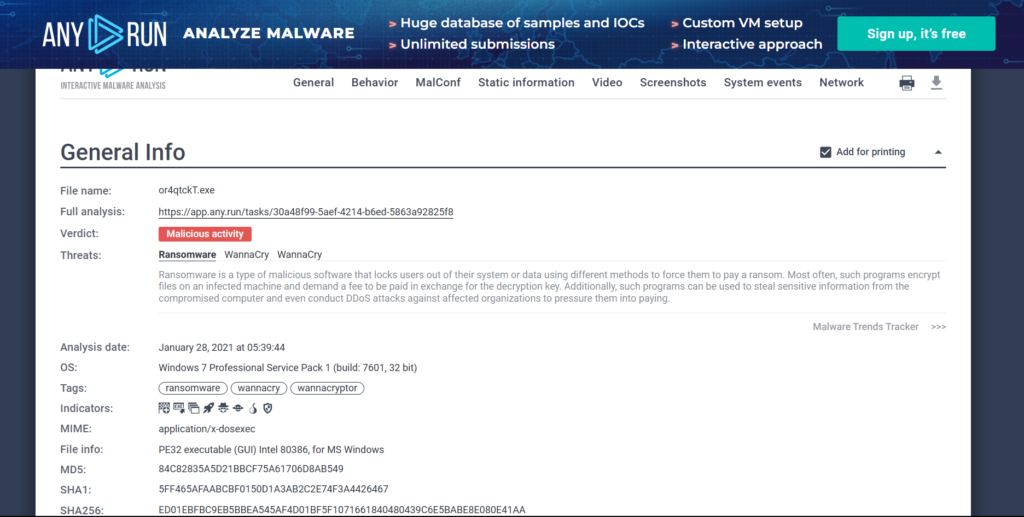
Can you identify what ransomware it is? (Do your research!)
A little search of the file name on Google brings us the answer:
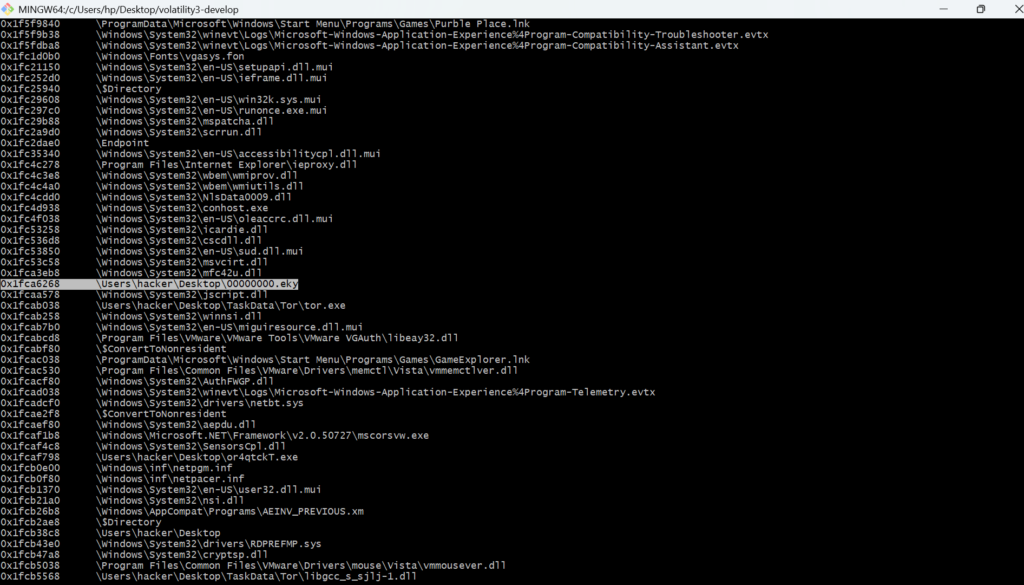
What is the filename for the file with the ransomware public key that was used to encrypt the private key? (.eky extension)
python3 vol.py -f infected.vmem windows.cmdline
python3 vol.py -f infected.vmem windows.dumpfiles –pid –dump-dir /path/to/output