Scenario
I’m Loner Varley, currently employed at Tech Innovator Inc., a cybersecurity start-up. Our company’s name may sound a bit whimsical, but our primary mission is to safeguard businesses from cyber threats and ensure their continuous operation. Ironically, we’ve recently faced allegations of security breaches. Yes, it’s quite ironic for a cybersecurity provider to fall victim to hacking; it almost feels worse than the reputation of LastPass. We’re certainly going through some challenging times, and sometimes it feels like we’re haunted by these incidents. I’ve become quite vigilant about our situation.
In my role as a Junior Forensics Analyst, I’ve observed some peculiar behavior from my colleague, Katy Tilf, who is an integral part of our two-person team. Lately, she’s been falling behind on her workload and missing important meetings, which is quite uncharacteristic of her. This situation has placed additional pressure on me, making me feel like I’m cleaning up after her, much like a janitor. What’s more frustrating is that our manager doesn’t seem to care much about her deteriorating performance, and this is on top of the already less-than-ideal circumstances at our start-up. It’s becoming increasingly exhausting for me to deal with this situation.
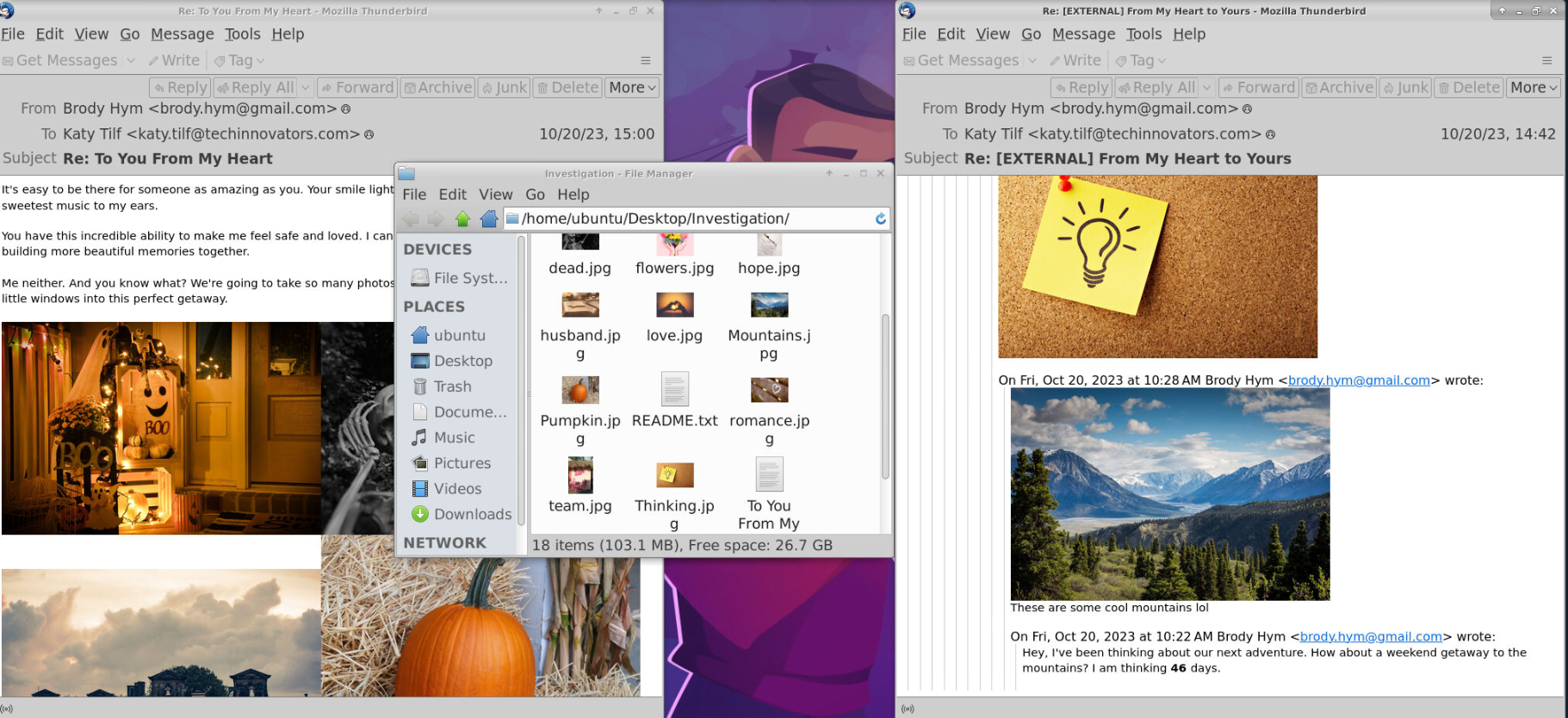
I’ve noticed that Katy is spending a lot of time using her Outlook email client. During a moment of curiosity, I observed her engaged in an extended email conversation with someone named Brody on her work PC. The strange thing is that Brody doesn’t work for our company, nor is he a client. Seizing an opportunity when Katy was away from her desk, I discreetly downloaded a copy of this email conversation. I’m determined to uncover the truth behind her actions and get to the bottom of this mystery.
Tools : Steghide, ExifTool, Ciphey , Thunderbird , Sublime, Cyberchef, Mitre Attack ID T1001.002
Q1. Fascinating, it appears the individual, Yurei, is employing data obfuscation, and it seems Katy concurs. What, then, is this enigmatic “Holy Code”? (Format: Holy Code)
The first step in this analysis is to examine both given emails. We’ll start by opening them in Thunderbird as well as in a plain text editor. The first email to analyze is the one with the subject “[EXTERNAL] From My Heart to Yours,” as it was delivered before the other. Upon inspection, it appears that all the attached photos contain embedded data. For instance, the file “Mountains.jpg” has data encoded within it using Base64 encryption.
The file Mountains.jpg is encoded in Base64.
Next, we analyzed the second email with the subject “Re: To You From My Heart” to determine if it exhibited the same behavior. This analysis confirmed that the same technique is present.
It seems that this case involves steganography. Steganography is the practice of concealing information within another medium to obscure its existence. Digitally, this often involves embedding messages or files inside images, audio, or other media without making the alteration obvious. The primary objective of steganography is to keep the act of communication hidden. To uncover the embedded information, we need to extract and analyze the hidden data within the photos. For this, we’ll use the tool Steghide.
Steghide is a tool that allows for decoding hidden content within a file, provided that the password used to encrypt the content is known. Upon reviewing the email content, we noticed that each reply contained a bolded word. These bolded words turned out to be the passwords required to unlock each file. This hypothesis was tested and confirmed to be correct.
Steghide can extract hidden content from a photo using the correct password. Each email reply contained a bolded word, which we hypothesized was the password. This was confirmed to be correct.
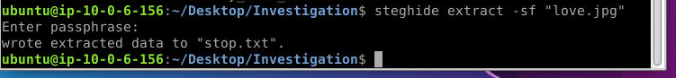
So, all the photos are downloaded and are analyzed by executing the following command and by entering the correct protective passphrase:
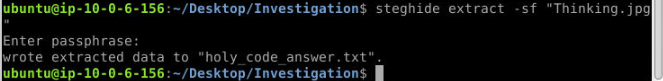
Extracting the content of the Thinking.jpg image reveals a file named holy_code_answer.txt, which contains data written in binary.
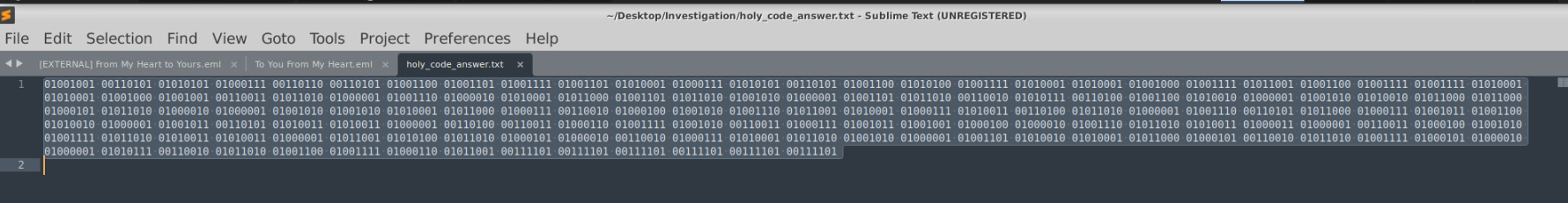
Opening the results in text editor shows binary code , so we will utilize cybershef to help us decipher it.
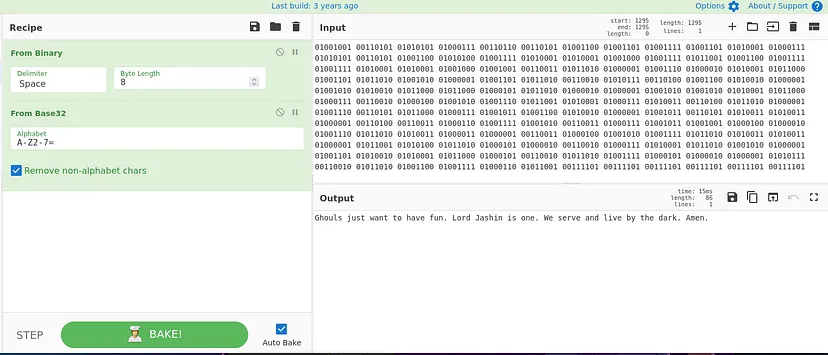
Using CyberChef, the binary data from holy_code_answer.txt was converted into ASCII. The first step involved decoding the binary into another encoding format, resulting in the following Base32 string: I5UG65LMOMQGU5LTOQQHOYLOOQQHI3ZANBQXMZJAMZ2W4LRAJRXXEZBAJJQXG2DJNYQGS4ZAN5XGKLRAK5SSA43FOJ3GKIDBNZSCA3DJOZSSAYTZEB2GQZJAMRQXE2ZOEBAW2ZLOFY======
This string is identified as Base32 due to its use of 32 characters (A–Z and 2–7) and the presence of padding with = to ensure a multiple of 8 in length. After decoding the Base32 into ASCII, the following text is obtained: “Ghouls just want to have fun. Lord Jashin is one. We serve and live by the dark. Amen.”
Q2. It appears Katy was far more treacherous than I had anticipated. She exposed our main server’s IP, which was what? (Format: X.X.X.X)
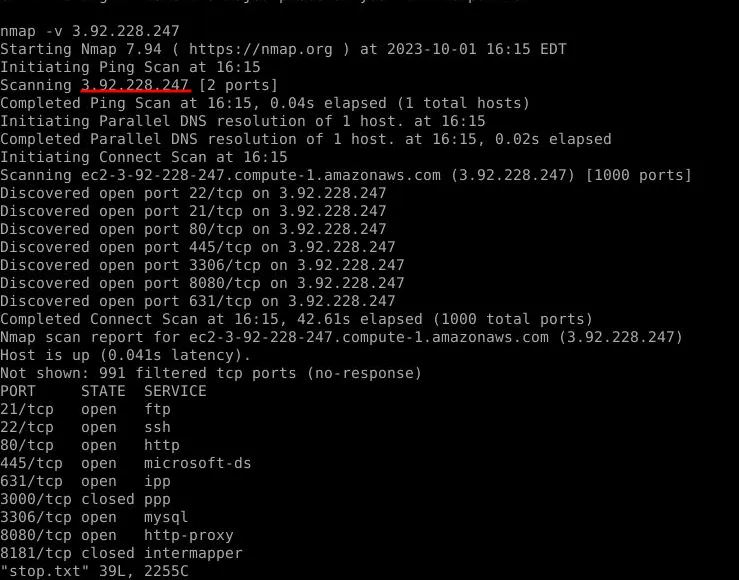
From the conversation between Yurei and Katy, it becomes evident that Yurei instructed Katy to execute an nmap scan on the main server. The IP address of this main server, 3.92.228.247, was extracted directly from the nmap scan results. Extracting the love.jpg gave us the nmap scan report.
Q3. That conniving snake. Is she scheming to betray us and then depart from the company on this particular date? (Format: Month DD, YYYY)
By analyzing the ciphered content hidden within the photos, we discover that Katy plans to leave the company on October 27, 2023. This information is found in the file crazy.txt, obtained after deciphering the husband.jpg image.
![]()
Q4) Who seems to be the leader of the criminal organization Yurei is affiliated with? (Format: Xxxx Xxxxxx)
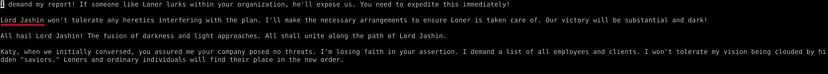
By analyzing the ciphered content hidden within the photos, it is revealed that Lord Jashin is the leader of the criminal organization. This information was found in the file eliminate.txt, obtained after deciphering the hope.jpg image.
Q5. Yurei seems to know where our PHP applications are running at. It seems like he was the one exploiting that RCE vulnerability. What was the name of it? (Format: Vulnerability Name)
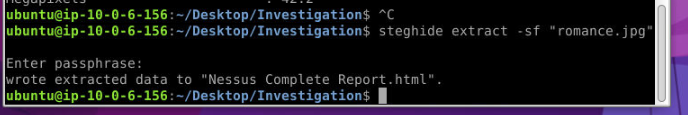
To extract the metadata of romance.jpg, which contains the Nessus report results and has a password stored within its metadata, you can use Exiftool with the following command:
This command will display all metadata associated with the photo, allowing you to locate the password needed to unlock the file.
exiftool romance.jpg
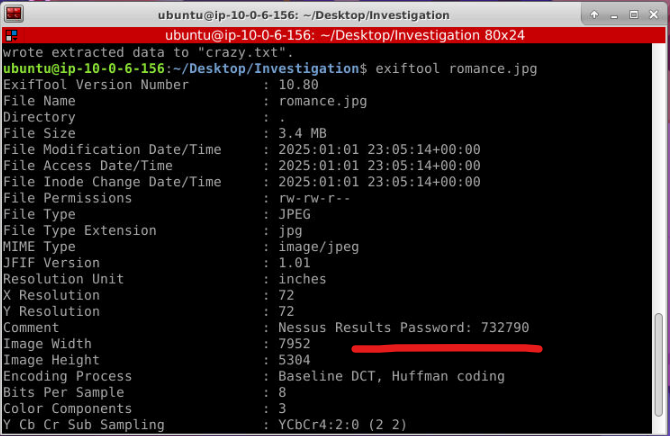
In the metadata, the “Comment” field contains the password required to decrypt romance.jpg using Steghide. The password is: 732790.
After deciphering romance.jpg, we obtain an HTML file named “Nessus Complete Report.html”. By reviewing the critical vulnerabilities listed in the report, we identify the Drupal Coder Module Deserialization RCE vulnerability. This vulnerability arises because the version of Drupal running on the remote web server is affected by a remote code execution issue in the Coder module, which allows attackers to execute arbitrary code on the server.
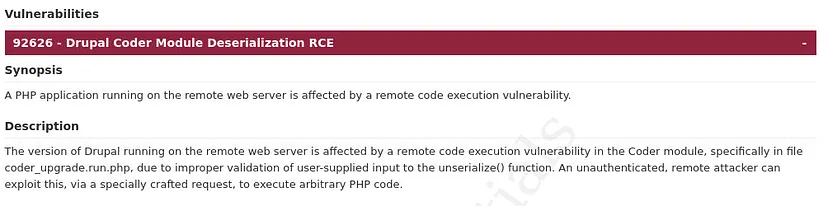
Q6. It seems our server has encountered yet another critical vulnerability. A particular module we are running has fallen victim to an information disclosure vulnerability, shedding light on our recent security breaches. Can you provide the CVE number associated with this vulnerability? (Format: CVE-XXXX-XXXX)
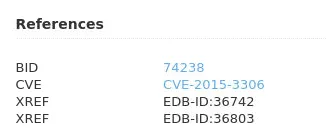
The next criticial vulnerability frm the nessus scan report is ProFTPD mod_copy Information Disclosure, which CVE can be found and is equal to CVE-2015–3306.
Q7. I’m genuinely surprised. What’s the reason behind our main server still running on an operating system that has reached its end of life (EOL)? It’s concerning how vulnerable we might be to attacks. Could you please provide the name of the operating system and its EOL date? (Format: OSName, Month DD, YYYY)
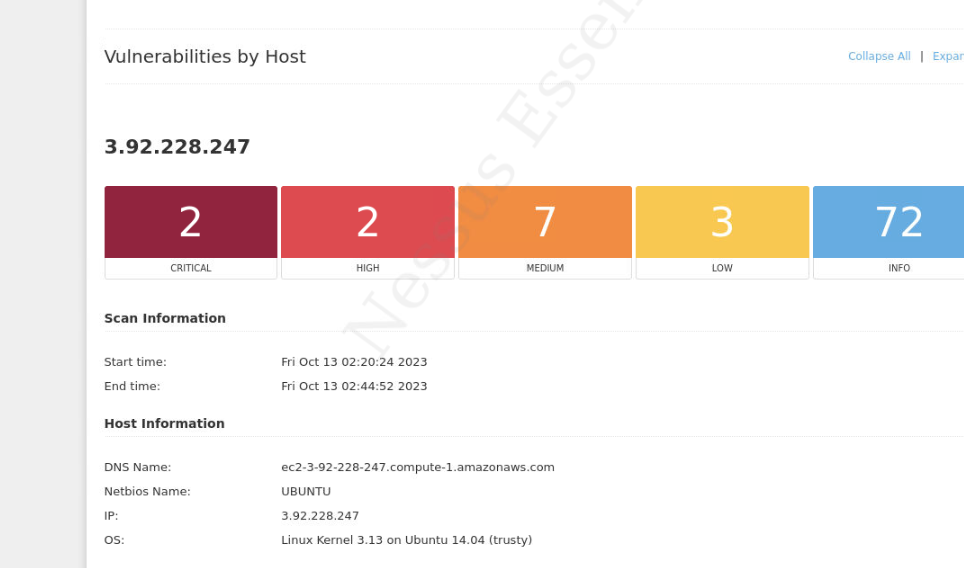
By analyzing the “Nessus Complete Report.html”, it is revealed that the operating system in use is Ubuntu 14.04. This version reached its End of Life (EOL) on April 25, 2019. The EOL date was verified through OSINT searches, highlighting that the system is no longer supported with security updates, leaving it vulnerable to exploitation.
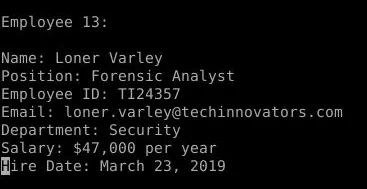
Q8. Intriguing! Despite handling half of the Security Department’s responsibilities, my salary significantly lagged behind that of my colleagues. After this, I’m certainly considering changing jobs. What was my current salary? (Format: $XX,XXX)
The last photo sent by Katy contains a compressed file named “Archive.zip”, which, when decompressed, reveals multiple files with confidential information. Among these files is “Tech_Innovators_Inc_Employee_List.txt”, which contains detailed employee information. From this file, we can extract Loner’s salary, which is $47,000 per year.
Q9. Katy has gone to the extent of sharing my report on HealthGuard with this adversary. Even though the incident is already public knowledge, the adversary is now aware that we’ve been backing their security department. What was the result of the cyber attack that targeted HealthGuard? (Format: Xxxx Xxxxxx)
After reading the report contained in the “Health_Guard_Hospitals_Breach1.txt” file, we can conclude that the result of the past cyberattack that targeted Health Guard was a Data breach.
![]()
Q10. After reading the report contained in the “Health_Guard_Hospitals_Breach1.txt” file, we can conclude that the result of the past cyberattack that targeted Health Guard was a Data breach.
After reading the content of the “Aero_Defense_Systems.txt” file we can conclude that AeroDefense followed Negotiations to attain a controlled resolution.
![]()
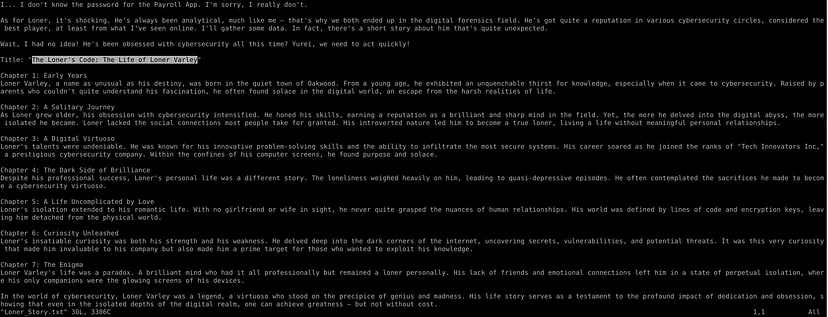
Q11. It appears they were well-informed about my inquisitiveness and conducted some background research on me. Yurei aims to erase my existence. Nevertheless, what is the title of my short story?
During the conversation, Yurei requests more information about me, the other cyberanalyst in the company. Katy responds by crafting a story saved in “Loner_Story.txt”. The title of this story is: “The Loner’s Code: The Life of Loner Varley.”
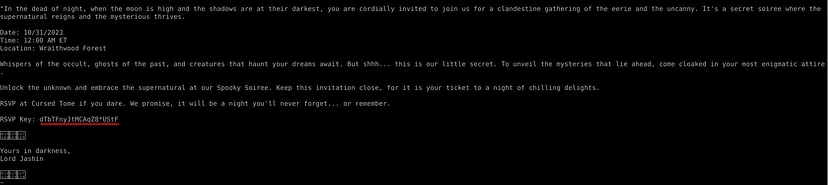
Q12. It appears Yurei has extended an invitation to Katy for an event taking place this Halloween in Wraitwood Forest, where the ghouls seem to be gathering, particularly under the banner of this “Lord Jashin.” I’m considering attending with some police officers as my companions. What is the RSVP Key for this event?
After deciphering the final photo, “Pumpkin.jpg,” using its secret password, “Samhain”—the ancient Celtic festival that precedes Halloween—we obtain the file “Jashin_Feast_Inv.txt”. This file contains an invitation to a secret meeting and includes the RSVP Key, which is: dTbTFnyJtMCAqZ8*UStF.