Scenario
1. According to Network Miner, what exploit attempt is being made on what protocol?
After we log in, we are presented with 2 folders: Tools contain Wireshark and Network Miner. Files contain sslkeylog and 2 Wireshark captures
When we use Network Miner to open the 2 captures files, we get error that PcapNg files are not supported.
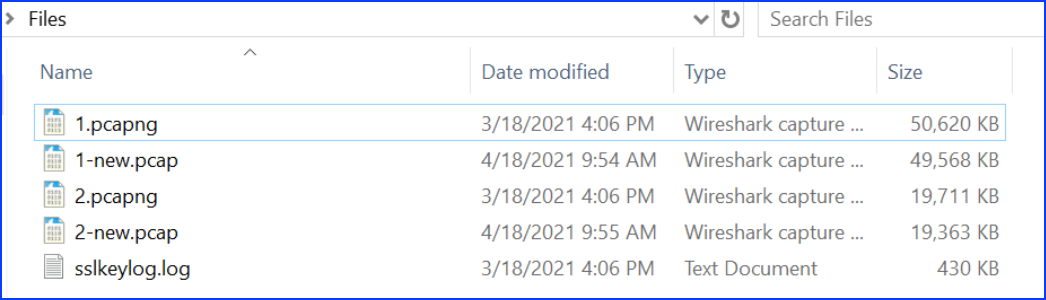
We open each of the Pcap files in Wireshark and save as older Pcap format:
For the 1 file, we see in the Anomalies tab the exploitation attempts:
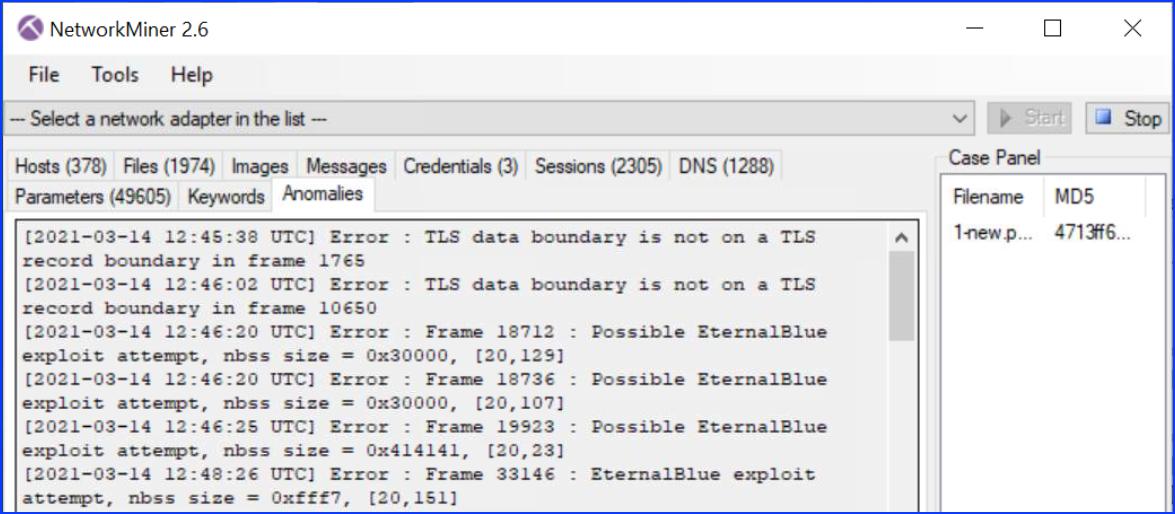
Answer: EternalBlue, SMB
2. What is the IP address of the machine responsible for conducting network scanning using Nmap?
From the 1st capture, in
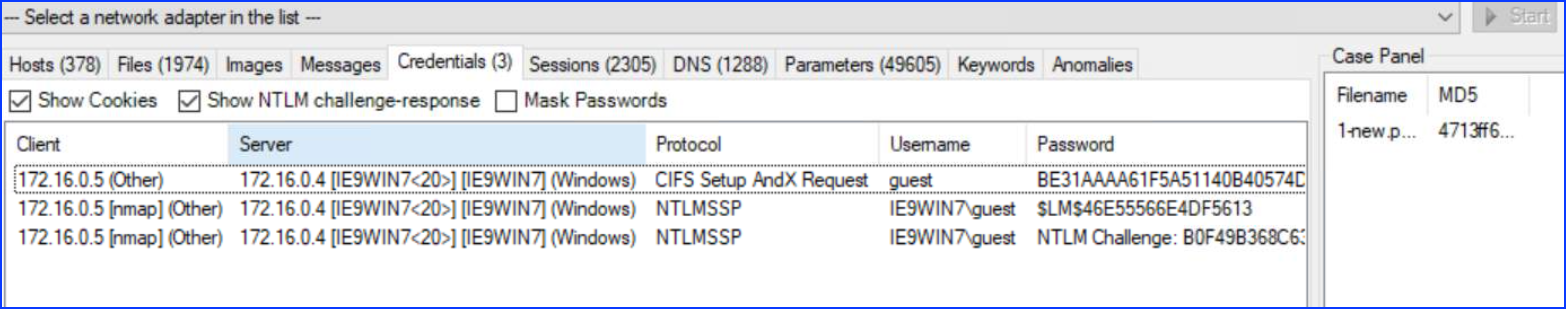
Answer: 172.16.0.5
3. Identify the Command-and-Control server. What are the hostname, MAC address, and listening port numbers?
We continue with network miner on Capture 1. We scroll down and we notice the IP 172.16.0.9 has sent many packets. Deploying the trees, we have the details:
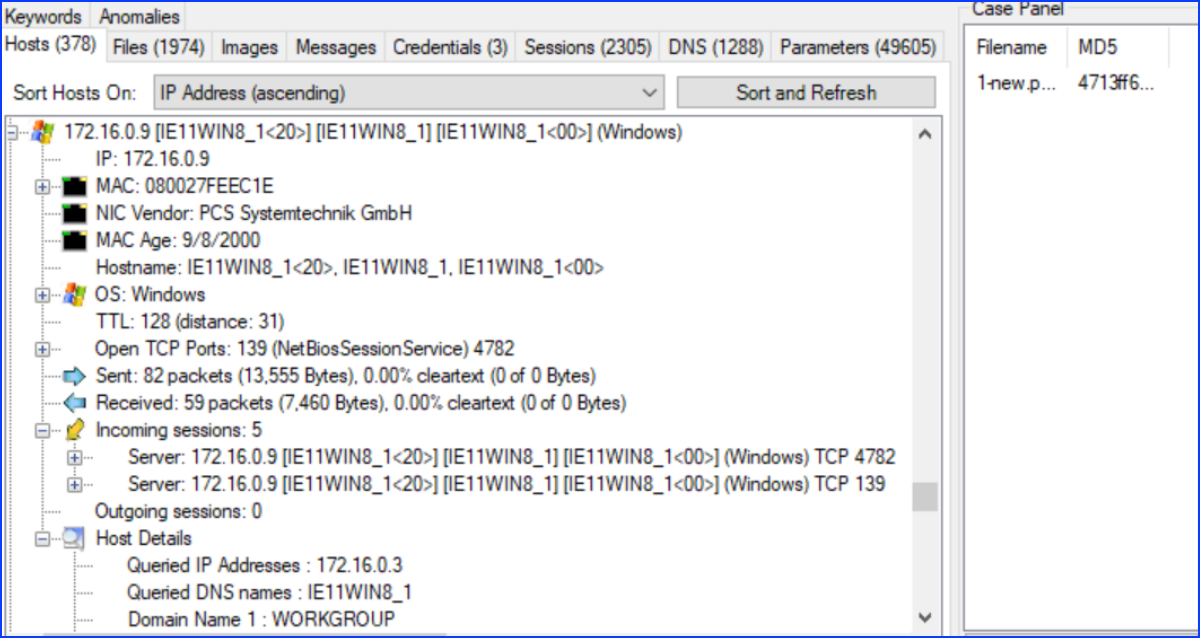
IE11WIN8_1, 080027FEEC1E, 4782, 139
4. What are the victim’s banking credentials?
Steps to Decrypt SSL/TLS Traffic and Extract Banking Credentials
1. Set Up Wireshark with SSL Key Log File
- Locate the SSL Key Log File:
- Use the provided
sslkeylogfile.
- Use the provided
- Configure Wireshark to Decrypt SSL/TLS:
- Open Wireshark and load the provided PCAP file.
- Navigate to:
Edit > Preferences > Protocols > TLS (or SSL).
- Under (Pre)-Master-Secret log filename, browse and add the
sslkeylogfile. - Save the settings.
After importing the file, we use this filter before continuing:
ip.src_host==172.16.0.4 && tls && http.request.method== "POST"Answer: christiww007, christismoneyworld$$
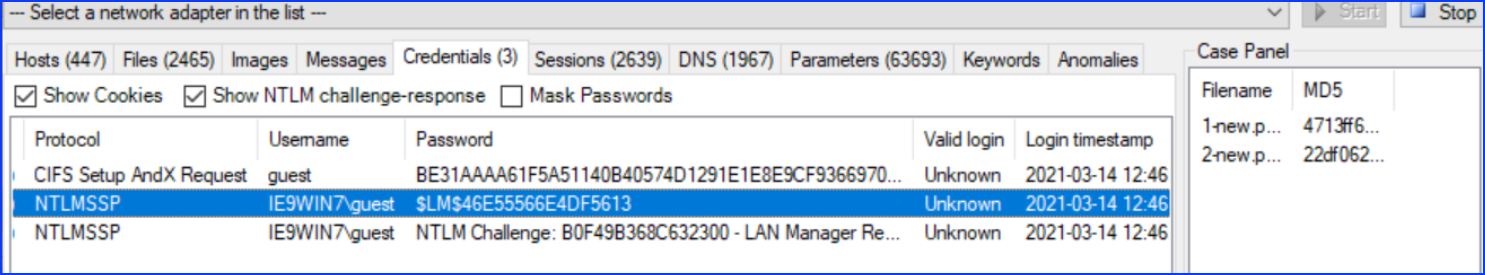
5. What is the observed NTLM Response to the challenge from VICTIM Machine?
From Network Miner, in the credentials tab, we can see the password field: