Scenario
You are provided with use-cases to conduct some proactive searches in ELK. Answer the following questions by using the information provided in README.txt.
Tools: – ELK (Elasticsearch, Logstash, and Kibana) — http://localhost:5601/ – CyberChef, – OSINT (whole World Wide Web) 🙂
ELK should start within 5 minutes, if not please try to start the services manually :
sudo systemctl start elasticsearch
sudo systemctl start kibana
sudo systemctl start logstash
Hunt 1 (1/3) – What is the IP address from which the suspicious brute force traffic is seen? (Format: X.X.X.X)
Brute Force
DetectedSource: winevent-security
We are investigating potential brute force attempts. To begin, we should focus on identifying failed logon attempts. The Event ID associated with failed logon attempts is 4625. Therefore, we can use the following query to find relevant events: Event_System_EventID : 4625
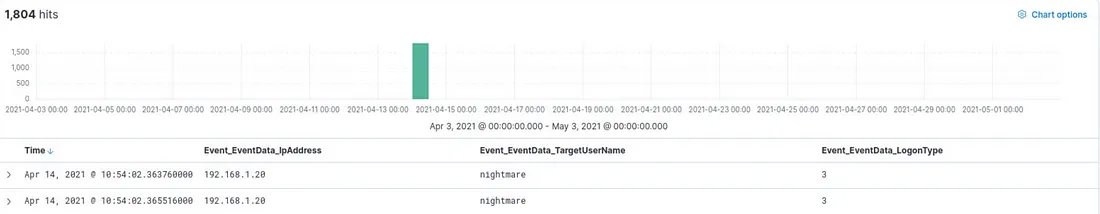
Now we can check Top values for Event_EventData_IpAddress field: Answer: 192.168.1.20
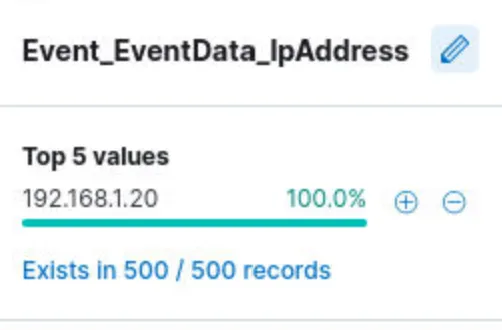
(2/3) — What is the observed logon type?
For this one we can check Top values for Event_EventData_LogonType field:
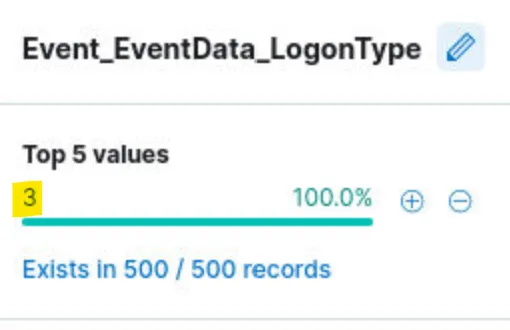
Quick look into documentation what does “3” in Logon type means:
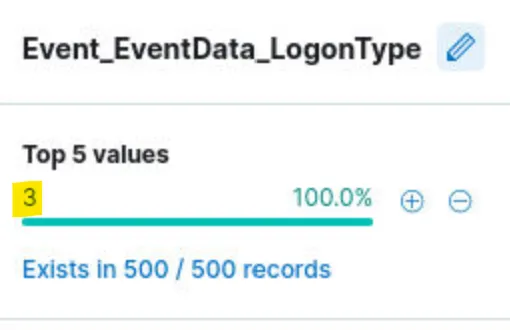
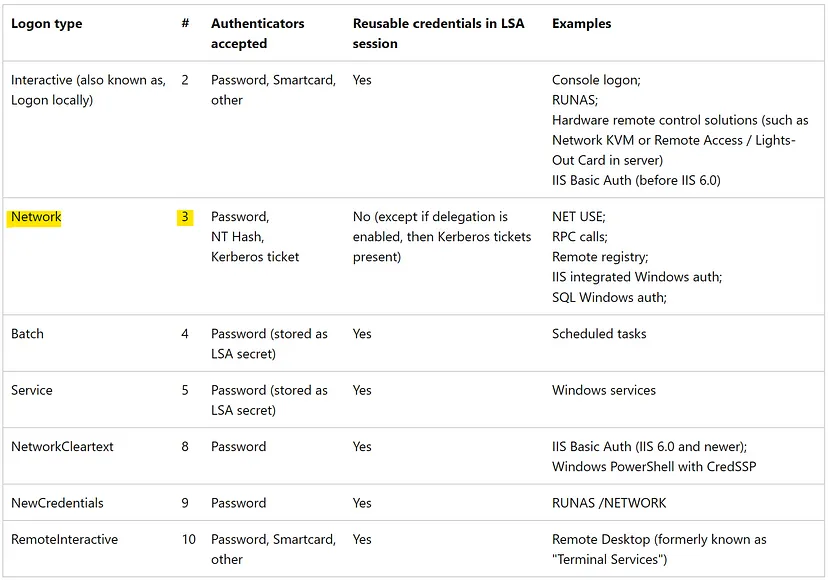
Answer: Network
(3/3) — What is the time of the first successful logon after the brute force?
Next, we will search for successful logon attempts, which are associated with Event ID: 4624. To refine our query, we will include specific criteria such as the IP address and target username. The updated query will look like this:
Event_System_EventID : “4624” AND Event_EventData_IpAddress: “192.168.1.20” AND Event_EventData_TargetUserName: “nightmare”

Answer (with given format): 14–04–2021 10:56:30
(1/2) — What is the full command used for bypassing the defender scan on the malicious file?
The key aspect of this investigation is identifying methods for “bypassing the Defender scan on the malicious file.” To achieve this, we should focus on identifying potential exclusions in Windows Defender settings. A good starting point would be reviewing the Windows Defender documentation and searching for references to the term “exclusion.” This will help us understand how exclusions are configured and potentially exploited for bypassing scans.
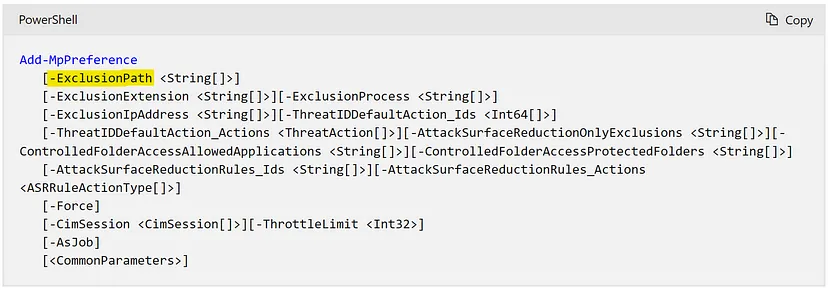
Now we have to create a simple query using “-ExclusionPath” parameter: “*-ExclusionPath*”
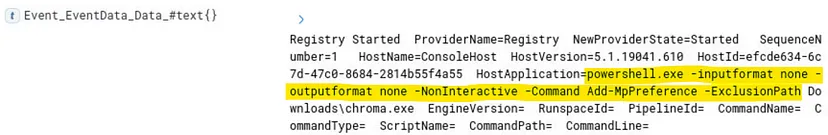
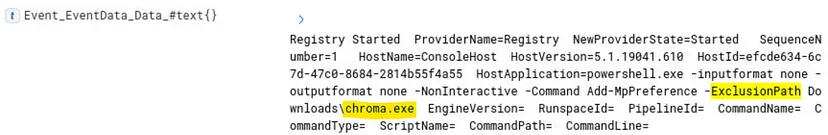
(2/2) — What is the filename of the malicious application?
Within same log we have the filename of the malicious application:
(1/2) — What is the domain name?
Let’s dive into Sysmon documentation to check which Event ID could be helpful with looking for domain names/queries:
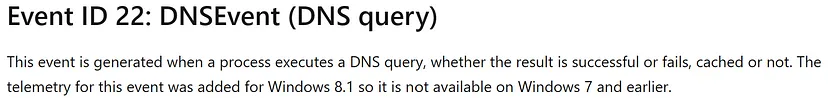
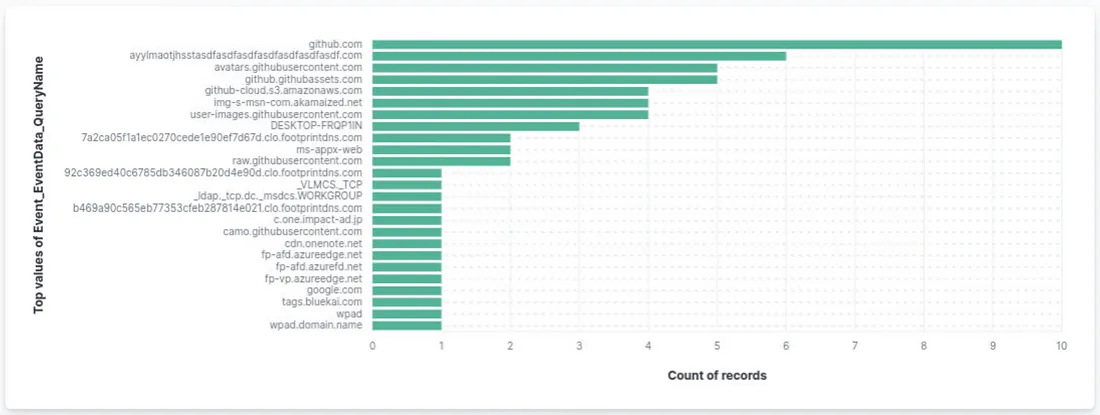
Now let’s use it to build our query: “Event_System_EventID: 22” and then use Event_EventData_QueryName field to visualize our results.
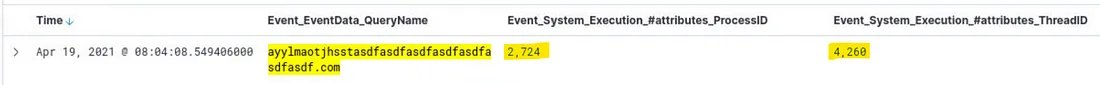
(2/2) — What is the Execution ProcessID and ThreadID?
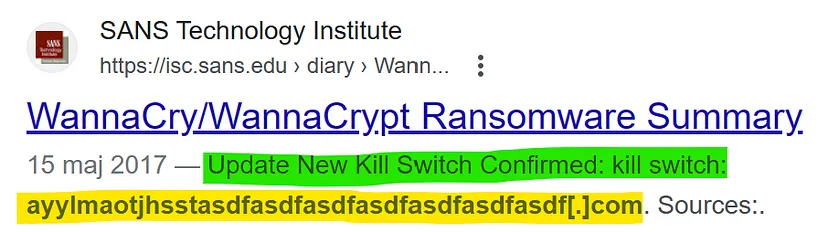
Let’s modify our previous query adding domain name: Event_System_EventID : 22 AND Event_EventData_QueryName: “ayylmaotjhsstasdfasdfasdfasdfasdfasdfasdf.com”:
(1/1) — What is the full path of the exe used for dumping password?
Let’s get back to Sysmon documentation once more. Which Event ID could be used for Password Dumping hunting?

If searching by Event IDs yields no results, we can attempt a last-resort query targeting common tools used for credential or password dumping. This approach may lead to a quick win. The query would look like this:
Event_EventData_Image : (mimi OR mimikatz OR procdump OR lsremora.dll OR lsremora64.dll OR dumpext.dll OR wceaux.dll OR “mimidrv.sys”)
This query searches for traces of well-known tools or files typically associated with credential dumping activities.
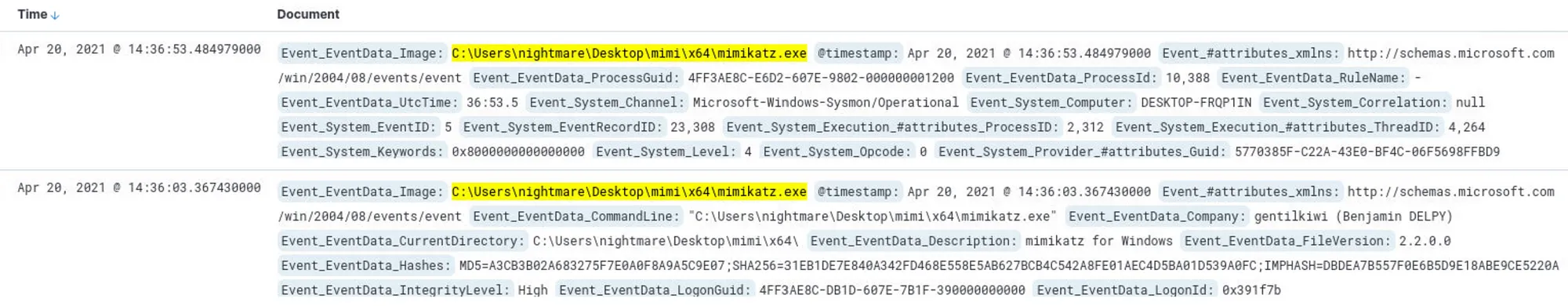
Answer: C:\Users\nightmare\Desktop\mimi\x64\mimikatz.exe
